Reverse proxy: Difference between revisions
No edit summary |
Reverted 1 edit by 212.147.41.58 (talk): Spam |
||
| (331 intermediate revisions by more than 100 users not shown) | |||
| Line 1: | Line 1: | ||
{{short description|Type of proxy server}} |
|||
A '''reverse proxy''' is a [[proxy server]] that is installed on a [[Server (computing)|server]] network or on network equipment. Typically, reverse proxies are used in front of [[Web server]]s. All connections coming from the Internet addressed to one of the Web servers are routed through the proxy server, which may either deal with the request itself or pass the request wholly or partially to the main web servers. This is useful to hide the real origin server from the client for security reasons, or to dispatch in-bound network traffic to a set of servers, presenting a single interface to the caller, by making [[Load balancing (computing)|load balancing]] among a cluster of servers.<ref>[http://rbt.phs.com.tw/manual/glossary.html#Reverse_Proxy A proxy server that appears to the client as if it is an origin server. This is useful to hide the real origin server from the client for security reasons, or to load balance.]</ref> |
|||
[[File:Reverse proxy h2g2bob.svg|thumb|right|280px|alt=A proxy server connecting the Internet to an internal network.|Example scenario: A client on the Internet (''cloud on the left'') makes a request to a '''reverse proxy''' server (''red oval in the middle''). The proxy inspects the request, determines that it is valid and that it does not have the requested resource in its own cache. It then forwards the request to some internal web server (''oval on the right''). The internal server delivers the requested resource back to the proxy, which in turn delivers it to the client. The client on the Internet is unaware of the internal network, and cannot tell whether it is communicating with a proxy or directly with a web server.]] |
|||
In [[computer network]]s, a '''reverse proxy''' or surrogate server is a [[proxy server]] that appears to any [[Client–server model|client]] to be an ordinary [[web server]], but in reality merely acts as an intermediary that forwards the client's requests to one or more ordinary web servers.<ref name="apache-forward-reverse">{{cite web |title=Forward and reverse proxies |url=http://httpd.apache.org/docs/current/mod/mod_proxy.html |url-status=live |archive-url=https://web.archive.org/web/20180828142409/http://httpd.apache.org/docs/current/mod/mod_proxy.html |archive-date=28 August 2018 |accessdate=26 August 2018 |publisher=The Apache Software Foundation}}</ref><ref> |
|||
In contrast, a ''forward proxy'' acts as a proxy for out-bound traffic. For example, an [[Internet service provider|ISP]] may use a proxy to forward [[HTTP]] traffic from its clients to external web servers on the Internet; it may also [[cache]] the results to improve performance.<ref>[http://rbt.phs.com.tw/manual/glossary.html#Proxy An intermediate server that sits between the client and the origin server. It accepts requests from clients, transmits those requests on to the origin server, and then returns the response from the origin server to the client. If several clients request the same content, the proxy can deliver that content from its cache, rather than requesting it from the origin server each time, thereby reducing response time.]</ref> |
|||
{{cite journal |last=Reese |first=Will |date=September 2008 |title=Nginx: the high-performance web server and reverse proxy |url=https://dl.acm.org/doi/fullHtml/10.5555/1412202.1412204 |journal=Linux Journal |issue=173 }} |
|||
</ref> Reverse proxies help increase scalability, performance, resilience, and security, but they also carry a number of risks. |
|||
Companies that run [[Web server|web servers]] often set up reverse proxies to facilitate the communication between an Internet user's [[Web browser|browser]] and the [[Web server|web servers]]. An important advantage of doing so is that the web servers can be hidden behind a [[Firewall (computing)|firewall]] on a company-internal network, and only the reverse proxy needs to be directly exposed to the Internet. Reverse proxy servers are implemented in popular [[Open-source software|open-source]] [[web server]]s. Dedicated reverse proxy servers are used by some of the biggest websites on the Internet. |
|||
There are several reasons for installing reverse proxy servers: |
|||
* Security: reverse proxies provide an additional layer of defense by masking the web server behind the proxy. Reverse proxies can also provide [[Application firewall]] features, to protect against common web-based attacks. |
|||
* Encryption / [[SSL acceleration]]: when [[secure website]]s are created, the [[Secure Sockets Layer|SSL]] encryption is sometimes not done by the Web server itself, but offloaded to a reverse proxy that may be equipped with SSL acceleration hardware. |
|||
| ⚫ | |||
* [[Cache|Caching]]: A reverse proxy can offload the Web servers by caching static content, such as images, as well as dynamic content, such as a web page rendered by [[PHP]]. [[Proxy cache]]s of this sort can often satisfy a considerable amount of website requests, greatly reducing the load on the central web server; another term is [[Web accelerator]]. This technique is also used for the [[Wikipedia#Software_and_hardware|Wikipedia servers]]. |
|||
* Compression: the proxy server can optimize and compress the content to speed up the load time. |
|||
| ⚫ | |||
A reverse proxy is capable of tracking all [[IP address|IP addresses]] requests that are relayed through it as well as reading and/or modifying any non-encrypted traffic. However, this implicitly means that a threat actor compromising the server could as well. |
|||
| ⚫ | |||
* [[Proxy server]] |
|||
Reverse proxies differ from [[forward proxy|forward proxies]], which are used when the client is restricted to a private, internal network and asks a forward proxy to retrieve resources from the public Internet. |
|||
Servers used commercially: |
|||
* [[Apache HTTP Server]] may be extended with mod_proxy to be used as a reverse proxy; a caching reverse proxy server may be configured using the mod_cache module in conjunction with mod_proxy.<ref name="apache-mod-proxy">[http://httpd.apache.org/docs/2.0/mod/mod_proxy.html mod_proxy - Apache HTTP Server]</ref> |
|||
== Uses == |
|||
* Apache [[Traffic Server]] - An open source, high-performance routing and caching server |
|||
Large websites and [[content delivery network]]s use reverse proxies, together with other techniques, to [[Load balancing (computing)|balance the load]] between internal servers. Reverse proxies can keep a [[Cache (computing)|cache]] of static content, which further reduces the load on these internal servers and the internal network. It is also common for reverse proxies to add features such as [[Data compression|compression]] or [[Transport Layer Security|TLS encryption]] to the communication channel between the client and the reverse proxy.<ref>{{Cite web |title=Proxy servers and tunneling |url=https://developer.mozilla.org/en-US/docs/Web/HTTP/Proxy_servers_and_tunneling |url-status=live |archive-url=https://web.archive.org/web/20201126050800/https://developer.mozilla.org/en-US/docs/Web/HTTP/Proxy_servers_and_tunneling |archive-date=26 November 2020 |access-date=2020-12-06 |website=MDN Web Docs |language=en}}</ref> |
|||
* [[ApplianSys#CACHEbox|CACHEbox]] is a high performance HTTP/HTTPS/FTP caching proxy appliance supporting reverse as well as forward deployment modes. |
|||
* [[Linoma_Software|GoAnywhere Gateway]] - An enhanced reverse proxy that allows FTP, FTPS, SFTP and HTTP services without exposing sensitive files in the DMZ or opening incoming ports into the internal network. |
|||
Reverse proxies can inspect [[HTTP header|HTTP headers]], which, for example, allows them to present a single [[IP address]] to the Internet while relaying requests to different internal servers based on the URL of the HTTP request. |
|||
* [[Internet Information Services]] 7.0 with URL Rewrite v2 and Application Request Routing can act as Reverse Proxy.<ref>{{cite web|url=http://learn.iis.net/page.aspx/659/reverse-proxy-with-url-rewrite-v2-and-application-request-routing/|title=Reverse Proxy with URL Rewrite v2 and Application Request Routing|date=July 16, 2009|accessdate=2010-03-12}}</ref> |
|||
* [[Lighttpd]] can be used as a reverse proxy with load balancing capabilities. |
|||
Reverse proxies can hide the existence and characteristics of [[origin server]]s. This can make it more difficult to determine the actual location of the origin server / website and, for instance, more challenging to initiate legal action such as takedowns or block access to the website, as the IP address of the website may not be immediately apparent. Additionally, the reverse proxy may be located in a different jurisdiction with different legal requirements, further complicating the takedown process. |
|||
* [[LiteSpeed Technologies Inc.|LiteSpeed]] Web Server can be used as a transparent reverse proxy server running in front of any web server or application server that supports HTTP protocol. |
|||
* [[Microsoft Forefront Threat Management Gateway]] (Forefront TMG), formerly known as Microsoft Internet Security and Acceleration Server (ISA Server) - A commercial proxy, firewall and caching solution by Microsoft. |
|||
[[Application firewall]] features can protect against common web-based attacks, like a [[denial-of-service attack|denial-of-service attack (DoS)]] or distributed denial-of-service attacks (DDoS). Without a reverse proxy, removing malware or initiating [[notice and take down|takedown]]s (while simultaneously dealing with the attack) on one's own site, for example, can be difficult. |
|||
* [[Nginx]] - Web and Reverse proxy server. |
|||
* [[Novell Access Manager]] is a commercial security solution which includes a reverse proxy, a policy based access manager and SSL VPN. All components use a LDAP like directory or federation with Liberty and others. |
|||
In the case of [[secure website]]s, a web server may not perform [[Transport Layer Security|TLS]] [[encryption]] itself, but instead offload the task to a reverse proxy that may be equipped with [[TLS acceleration]] hardware. (See [[TLS termination proxy]].) |
|||
* [[Perlbal]] is a Perl-based reverse proxy load balancer and web server. |
|||
* [[Pound (networking)|Pound]], a lightweight open source reverse proxy. |
|||
| ⚫ | A reverse proxy can [[load balancing (computing)|distribute the load]] from incoming requests to several servers, with each server supporting its own application area. In the case of reverse proxying [[web server]]s, the reverse proxy may have to rewrite the [[URL]] in each incoming request in order to match the relevant internal location of the requested resource. |
||
* [[Secure_Computing#Web_Security_products|McAfee Web Gateway]] is a product that can act as a reverse proxy. It also provides SSL decryption, caching, AV, Anti-Spam and other threat detection techniques. |
|||
* [[Squid (software)|Squid]] is a proxy server that may be installed in a reverse proxy configuration. |
|||
A reverse proxy can reduce load on its origin servers by [[web cache|caching]] [[Static web page|static content]] and [[Dynamic web page|dynamic content]], known as [[web accelerator|web acceleration]]. Proxy caches of this sort can often satisfy a considerable number of website requests, greatly reducing the load on the origin server(s). |
|||
* [[Stunnel]] can be used as a local SSL reverse proxy. |
|||
* [[Sun Java System Web Server]] includes reverse proxy module with load balancing capabilities. |
|||
A reverse proxy can optimize content by [[HTTP compression|compressing]] it in order to speed up loading times. |
|||
* [[Varnish cache|Varnish]] is a performance-focused open source reverse proxy. It has a policy configuration language to allow extension. It features [[Edge Side Includes|ESI]], SaintMode, DNS director and native support for In-line C. |
|||
* [[WinGate (computing)|WinGate]] supports reverse-proxying with SSL, authentication, and multiple virtual hosts. |
|||
| ⚫ | In a technique named "spoon-feeding",<ref name="spoon-feeding">{{cite web|url=http://wiki.squid-cache.org/SpoonFeeding|title=squid-cache wiki entry on "SpoonFeeding"|publisher=Francesco Chemolli|access-date=9 February 2011|archive-date=25 January 2019|archive-url=https://web.archive.org/web/20190125220423/https://wiki.squid-cache.org/SpoonFeeding|url-status=dead}}</ref> a dynamically generated page can be produced all at once and served to the reverse proxy, which can then return it to the client a little bit at a time. The program that generates the page need not remain open, thus releasing server resources during the possibly extended time the client requires to complete the transfer. |
||
* [[Zeus Web Server|Zeus]] is a product that can function as both a forward and reverse proxy, as well as content load balancer. |
|||
Reverse proxies can operate wherever multiple web-servers must be accessible via a single public IP address. The web servers listen on different ports in the same machine, with the same local IP address or, possibly, on different machines with different local IP addresses. The reverse proxy analyzes each incoming request and delivers it to the right server within the [[local area network]]. |
|||
Reverse proxies can perform [[A/B testing]] and [[multivariate testing in marketing|multivariate testing]] without requiring application code to handle the logic of which version is served to a client. |
|||
A reverse proxy can add access [[authentication]] to a web server that does not have any authentication.<ref>{{cite web|title=Possible to add basic HTTP access authentication via HAProxy?|url=http://serverfault.com/questions/239749/possible-to-add-basic-http-access-authentication-via-haproxy|website=serverfault.com|access-date=27 April 2016|archive-date=4 October 2018|archive-url=https://web.archive.org/web/20181004191559/https://serverfault.com/questions/239749/possible-to-add-basic-http-access-authentication-via-haproxy|url-status=live}}</ref><ref>{{Cite web |title=forward_auth (Caddyfile directive) - Caddy Documentation |url=https://caddyserver.com/docs/caddyfile/directives/forward_auth#examples |access-date=2022-05-22 |website=caddyserver.com}}</ref> |
|||
== Risks == |
|||
When the transit traffic is [[Encryption|encrypted]] and the reverse proxy needs to filter/cache/compress or otherwise modify or improve the traffic, the proxy first must decrypt and re-encrypt communications. This requires the proxy to possess the [[TLS certificate]] and its corresponding private key, extending the number of systems that can have access to non-encrypted data and making it a more valuable target for attackers. |
|||
The vast majority of external [[List of data breaches|data breaches]] happen either when hackers succeed in abusing an existing reverse proxy that was intentionally deployed by an organisation, or when hackers succeed in [[Superuser|converting]] an existing Internet-facing server into a reverse proxy server. Compromised or converted systems allow external attackers to specify where they want their attacks proxied to, enabling their access to internal networks and systems. |
|||
Applications that were developed for the internal use of a company are not typically hardened to public standards and are not necessarily designed to withstand all hacking attempts. When an organisation allows external access to such internal applications via a reverse proxy, they might unintentionally increase their own attack surface and invite hackers. |
|||
If a reverse proxy is not configured to filter attacks or it does not receive daily updates to keep its attack signature database up to date, a [[Zero-day (computing)|zero-day]] vulnerability can pass through unfiltered, enabling attackers to gain control of the system(s) that are behind the reverse proxy server. |
|||
Using the reverse proxy of a third party (e.g., [[Cloudflare]], [[Imperva]]) places the entire [[CIA triad|triad of confidentiality, integrity and availability]] in the hands of the third party who operates the proxy. |
|||
If a reverse proxy is fronting many different [[Domain name|domains]], its outage (e.g., by a misconfiguration or DDoS attack) could bring down all fronted domains.<ref>{{Cite web|title=Cloudflare outage knocks out major sites and services, including Discord|url=https://finance.yahoo.com/news/cloudflare-outage-knocks-major-sites-170213763.html|access-date=2020-12-14|website=finance.yahoo.com|language=en-US|archive-date=22 June 2020|archive-url=https://web.archive.org/web/20200622044745/https://finance.yahoo.com/news/cloudflare-outage-knocks-major-sites-170213763.html|url-status=dead}}</ref> |
|||
Reverse proxies can also become a [[single point of failure]] if there is no other way to access the back end server. |
|||
| ⚫ | |||
* [[Network address translation]] |
|||
== References == |
== References == |
||
{{reflist}} |
{{reflist}} |
||
{{Use dmy dates|date=November 2017}} |
|||
| ⚫ | |||
<!-- Categories --> |
|||
| ⚫ | |||
{{DEFAULTSORT:Reverse Proxy}} |
|||
| ⚫ | |||
[[Category:Network performance]] |
|||
[[Category:Internet architecture]] |
|||
<!-- Interwikies --> |
|||
[[cs:Reverzní proxy server]] |
|||
| ⚫ | |||
[[ja:リバースプロキシ]] |
|||
[[pt:Proxy reverso]] |
|||
[[tr:Vekil sunucu]] |
|||
Latest revision as of 17:34, 18 December 2024
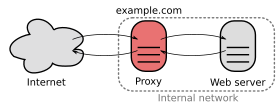
In computer networks, a reverse proxy or surrogate server is a proxy server that appears to any client to be an ordinary web server, but in reality merely acts as an intermediary that forwards the client's requests to one or more ordinary web servers.[1][2] Reverse proxies help increase scalability, performance, resilience, and security, but they also carry a number of risks.
Companies that run web servers often set up reverse proxies to facilitate the communication between an Internet user's browser and the web servers. An important advantage of doing so is that the web servers can be hidden behind a firewall on a company-internal network, and only the reverse proxy needs to be directly exposed to the Internet. Reverse proxy servers are implemented in popular open-source web servers. Dedicated reverse proxy servers are used by some of the biggest websites on the Internet.
A reverse proxy is capable of tracking all IP addresses requests that are relayed through it as well as reading and/or modifying any non-encrypted traffic. However, this implicitly means that a threat actor compromising the server could as well.
Reverse proxies differ from forward proxies, which are used when the client is restricted to a private, internal network and asks a forward proxy to retrieve resources from the public Internet.
Uses
[edit]Large websites and content delivery networks use reverse proxies, together with other techniques, to balance the load between internal servers. Reverse proxies can keep a cache of static content, which further reduces the load on these internal servers and the internal network. It is also common for reverse proxies to add features such as compression or TLS encryption to the communication channel between the client and the reverse proxy.[3]
Reverse proxies can inspect HTTP headers, which, for example, allows them to present a single IP address to the Internet while relaying requests to different internal servers based on the URL of the HTTP request.
Reverse proxies can hide the existence and characteristics of origin servers. This can make it more difficult to determine the actual location of the origin server / website and, for instance, more challenging to initiate legal action such as takedowns or block access to the website, as the IP address of the website may not be immediately apparent. Additionally, the reverse proxy may be located in a different jurisdiction with different legal requirements, further complicating the takedown process.
Application firewall features can protect against common web-based attacks, like a denial-of-service attack (DoS) or distributed denial-of-service attacks (DDoS). Without a reverse proxy, removing malware or initiating takedowns (while simultaneously dealing with the attack) on one's own site, for example, can be difficult.
In the case of secure websites, a web server may not perform TLS encryption itself, but instead offload the task to a reverse proxy that may be equipped with TLS acceleration hardware. (See TLS termination proxy.)
A reverse proxy can distribute the load from incoming requests to several servers, with each server supporting its own application area. In the case of reverse proxying web servers, the reverse proxy may have to rewrite the URL in each incoming request in order to match the relevant internal location of the requested resource.
A reverse proxy can reduce load on its origin servers by caching static content and dynamic content, known as web acceleration. Proxy caches of this sort can often satisfy a considerable number of website requests, greatly reducing the load on the origin server(s).
A reverse proxy can optimize content by compressing it in order to speed up loading times.
In a technique named "spoon-feeding",[4] a dynamically generated page can be produced all at once and served to the reverse proxy, which can then return it to the client a little bit at a time. The program that generates the page need not remain open, thus releasing server resources during the possibly extended time the client requires to complete the transfer.
Reverse proxies can operate wherever multiple web-servers must be accessible via a single public IP address. The web servers listen on different ports in the same machine, with the same local IP address or, possibly, on different machines with different local IP addresses. The reverse proxy analyzes each incoming request and delivers it to the right server within the local area network.
Reverse proxies can perform A/B testing and multivariate testing without requiring application code to handle the logic of which version is served to a client.
A reverse proxy can add access authentication to a web server that does not have any authentication.[5][6]
Risks
[edit]When the transit traffic is encrypted and the reverse proxy needs to filter/cache/compress or otherwise modify or improve the traffic, the proxy first must decrypt and re-encrypt communications. This requires the proxy to possess the TLS certificate and its corresponding private key, extending the number of systems that can have access to non-encrypted data and making it a more valuable target for attackers.
The vast majority of external data breaches happen either when hackers succeed in abusing an existing reverse proxy that was intentionally deployed by an organisation, or when hackers succeed in converting an existing Internet-facing server into a reverse proxy server. Compromised or converted systems allow external attackers to specify where they want their attacks proxied to, enabling their access to internal networks and systems.
Applications that were developed for the internal use of a company are not typically hardened to public standards and are not necessarily designed to withstand all hacking attempts. When an organisation allows external access to such internal applications via a reverse proxy, they might unintentionally increase their own attack surface and invite hackers.
If a reverse proxy is not configured to filter attacks or it does not receive daily updates to keep its attack signature database up to date, a zero-day vulnerability can pass through unfiltered, enabling attackers to gain control of the system(s) that are behind the reverse proxy server.
Using the reverse proxy of a third party (e.g., Cloudflare, Imperva) places the entire triad of confidentiality, integrity and availability in the hands of the third party who operates the proxy.
If a reverse proxy is fronting many different domains, its outage (e.g., by a misconfiguration or DDoS attack) could bring down all fronted domains.[7]
Reverse proxies can also become a single point of failure if there is no other way to access the back end server.
See also
[edit]References
[edit]- ^ "Forward and reverse proxies". The Apache Software Foundation. Archived from the original on 28 August 2018. Retrieved 26 August 2018.
- ^ Reese, Will (September 2008). "Nginx: the high-performance web server and reverse proxy". Linux Journal (173).
- ^ "Proxy servers and tunneling". MDN Web Docs. Archived from the original on 26 November 2020. Retrieved 6 December 2020.
- ^ "squid-cache wiki entry on "SpoonFeeding"". Francesco Chemolli. Archived from the original on 25 January 2019. Retrieved 9 February 2011.
- ^ "Possible to add basic HTTP access authentication via HAProxy?". serverfault.com. Archived from the original on 4 October 2018. Retrieved 27 April 2016.
- ^ "forward_auth (Caddyfile directive) - Caddy Documentation". caddyserver.com. Retrieved 22 May 2022.
- ^ "Cloudflare outage knocks out major sites and services, including Discord". finance.yahoo.com. Archived from the original on 22 June 2020. Retrieved 14 December 2020.
