Web of trust: Difference between revisions
No edit summary |
Chimelites (talk | contribs) m As far as I can ascertain, the gswot link has been dead for multiple months, according to the wayback machine. |
||
| (172 intermediate revisions by more than 100 users not shown) | |||
| Line 1: | Line 1: | ||
{{short description|Mechanism for authenticating cryptographic keys}} |
|||
{{For|the internet security website|WOT Services}} |
{{For|the internet security website|WOT Services}} |
||
{{more citations needed|date=May 2023}} |
|||
[[File:Web_of_Trust-en.svg|thumb|upright=1.35|Schematic diagram of a Web of Trust]] |
|||
This site is most likely a scam. If you suddenly find an unjustified and incorrect review, such as your website being labelled as a paid per click advertising site, they will not remove the review. Instead they will ask you to register with them and claim the site as the site owner. This involves inserting a piece of code into your website that they can then monitor for whatever reason. Scams like this are all too often used to to increase their "member" numbers, which can then potentially be sold to advertisers or email mail farmers. The reviews are most likely made by a bot. |
|||
| ⚫ | In [[cryptography]], a '''web of trust''' is a concept used in [[Pretty Good Privacy|PGP]], [[GNU Privacy Guard|GnuPG]], and other [[OpenPGP]]-compatible systems to establish the [[Authentication|authenticity]] of the binding between a [[public key]] and its owner. Its decentralized [[trust metric#Formal metrics|trust model]] is an alternative to the centralized trust model of a [[public key infrastructure]] (PKI), which relies exclusively on a [[certificate authority]] (or a hierarchy of such).<ref>{{Cite journal |last=Chien |first=Hung-Yu |date=2021-08-19 |title=Dynamic Public Key Certificates with Forward Secrecy |journal=Electronics |language=en |volume=10 |issue=16 |pages=2009 |doi=10.3390/electronics10162009 |issn=2079-9292|doi-access=free }}</ref> As with computer networks, there are many independent webs of trust, and any user (through their [[public key certificate]]) can be a part of, and a link between, multiple webs. |
||
| ⚫ | |||
Around 4,241,223 reviews have been added by a superhuman member called GURBL who has been a member since 2010. That's a staggering 68,406 reviews per month, or 2,280 reviews per day. To spend that much time in front of a computer GURBL would need to be a total computer geek, allowing for the average time spent masturbating daily by a computer geek that amount of 'reviewing' would not be possible. It is therefore entirely likely GURBL is a bot. |
|||
| ⚫ | {{quotation|As time goes on, you will accumulate keys from other people that you may want to designate as trusted introducers. Everyone else will each choose their own trusted introducers. And everyone will gradually accumulate and distribute with their key a collection of certifying signatures from other people, with the expectation that anyone receiving it will trust at least one or two of the signatures. This will cause the emergence of a decentralized fault-tolerant web of confidence for all public keys.}} |
||
Note the use of the word [[emergence]] in this context. The web of trust makes use of the concept of emergence. |
|||
In light of their appauling service towards site owners and prospective customers, anyone with sense would not trust this company if they said it was dark at midnight. |
|||
| ⚫ | |||
Beware, do not fall for this scam |
|||
| ⚫ | All OpenPGP-compliant implementations include a certificate [[vetting]] scheme to assist with this; its operation has been termed a web of trust. OpenPGP certificates (which include one or more public keys along with owner information) can be digitally signed by other users who, by that act, endorse the association of that public key with the person or entity listed in the certificate. This is commonly done at [[key signing party|key signing parties]].<ref>{{Cite book|last1=Ulrich|first1=Alexander|last2=Holz|first2=Ralph|last3=Hauck|first3=Peter|last4=Carle|first4=Georg|title=Computer Security – ESORICS 2011 |chapter=Investigating the OpenPGP Web of Trust |date=2011|editor-last=Atluri|editor-first=Vijay|editor2-last=Diaz|editor2-first=Claudia|series=Lecture Notes in Computer Science|volume=6879 |language=en|location=Berlin, Heidelberg|publisher=Springer|pages=489–507|doi=10.1007/978-3-642-23822-2_27|isbn=978-3-642-23822-2|doi-access=free}}</ref> |
||
| ⚫ | OpenPGP-compliant implementations also include a vote counting scheme which can be used to determine which public key – owner association a user will trust while using PGP. For instance, if three partially trusted endorsers have vouched for a certificate (and so its included public key – owner [[Data binding|binding]]), or if one fully trusted endorser has done so, the association between owner and public key in that certificate will be trusted to be correct. The parameters are user-adjustable (e.g., no partials at all, or perhaps six partials) and can be completely bypassed if desired. |
||
| ⚫ | The scheme is flexible, unlike most public key infrastructure designs, and leaves trust decisions in the hands of individual users. It is not perfect and requires both caution and intelligent supervision by users. Essentially all PKI designs are less flexible and require users to follow the trust endorsement of the PKI generated, certificate authority (CA)-signed, certificates. |
||
===Simplified explanation=== |
|||
| ⚫ | |||
| ⚫ | Senders encrypt their information with the recipient's public key, and only the recipient's private key will decrypt it. Each sender then digitally signs the encrypted information with their private key. When the recipient verifies the received encrypted information against the sender's public key, they can confirm that it is from the sender. Doing this will ensure that the encrypted information came from the specific user and has not been tampered with, and only the intended recipient can decrypt the information (because only they know their private key). |
||
| ⚫ | |||
| ⚫ | Unlike WOT, a typical [[X.509]] PKI enables each certificate to be signed by a single party: a [[certificate authority]] (CA). The CA's certificate may itself be signed by a different CA, all the way up to a 'self-signed' [[root certificate]]. Root certificates must be available to those who use a lower-level CA certificate and so are typically distributed widely. They are for instance, distributed with such applications as browsers and email clients. In this way [[Transport Layer Security|SSL/TLS]]-protected Web pages, email messages, etc. can be authenticated without requiring users to manually install root certificates. Applications commonly include over one hundred root certificates from dozens of PKIs, thus by default bestowing trust throughout the hierarchy of certificates which lead back to them. |
||
WOT favors the decentralization of trust anchors to prevent a single point of failure from compromising the CA hierarchy.<ref>{{cite web|url=https://blog.mozilla.org/security/2011/08/29/fraudulent-google-com-certificate/|access-date=29 August 2011|last=Nightingale|first=Johnathan|title=Fraudulent *.google.com Certificate}}</ref> |
|||
==Problems== |
|||
=== Loss of private keys === |
|||
| ⚫ | The OpenPGP web of trust is essentially unaffected by such things as company failures, and has continued to function with little change. However, a related problem does occur: users, whether individuals or organizations, who lose track of a private key can no longer decrypt messages sent to them produced using the matching public key found in an OpenPGP certificate. Early PGP certificates did not include expiry dates, and those certificates had unlimited lives. Users had to prepare a signed cancellation certificate against the time when the matching private key was lost or compromised. One very prominent cryptographer is still getting messages encrypted using a public key for which he long ago lost track of the private key.<ref>{{cite book|last1=Ferguson|first1=Niels|last2=Schneier|first2=Bruce|title=Practical Cryptography|publisher=Wiley|year=2003|isbn=978-0471223573|pages=333|quote=Bruce lost a PGP key almost a decade ago; he still gets email encrypted with the corresponding certificate.}}</ref> They can't do much with those messages except discard them after notifying the sender that they were unreadable and requesting resending with a public key for which they still have the matching private key. Later PGP, and all OpenPGP compliant certificates include expiry dates which automatically preclude such troubles (eventually) when used sensibly. This problem can also be easily avoided by the use of "designated revokers", which were introduced in the early 1990s. A key owner may designate a third party that has permission to revoke the key owner's key (in case the key owner loses his own private key and thus loses the ability to revoke his own public key). |
||
=== Public key authenticity check === |
|||
| ⚫ | In [[cryptography]], a '''web of trust''' is a concept used in [[Pretty Good Privacy|PGP]], [[GNU Privacy Guard|GnuPG]], and other [[OpenPGP]]-compatible systems to establish the authenticity of the binding between a public key and its owner. Its decentralized trust model is an alternative to the centralized trust model of a [[public key infrastructure]] (PKI), which relies exclusively on a [[certificate authority]] (or a hierarchy of such). As with computer networks, there are many independent webs of trust, and any user (through their [[ |
||
| ⚫ | A non-technical, social difficulty with a Web of Trust like the one built into PGP/OpenPGP type systems is that every web of trust without a central controller (e.g., a [[Certificate authority|CA]]) depends on other users for trust. Those with new certificates (i.e., produced in the process of generating a new key pair) will not likely be readily trusted by other users' systems, that is by those they have not personally met, until they find enough endorsements for the new certificate. This is because many other Web of Trust users will have their certificate vetting set to require one or more fully trusted endorsers of an otherwise unknown certificate (or perhaps several partial endorsers) before using the public key in that certificate to prepare messages, believe signatures, etc. |
||
| ⚫ | Despite the wide use of OpenPGP compliant systems and easy availability of on-line multiple [[key server (cryptographic)|key server]]s, it is possible in practice to be unable to readily find someone (or several people) to endorse a new certificate (e.g., by comparing physical identification to key owner information and then digitally signing the new certificate). Users in remote areas or undeveloped ones, for instance, may find other users scarce. And, if the other's certificate is also new (and with no or few endorsements from others), then its signature on any new certificate can offer only marginal benefit toward becoming trusted by still other parties' systems and so able to securely exchange messages with them. [[Key signing party|Key signing parties]] are a relatively popular mechanism to resolve this problem of finding other users who can install one's certificate in existing webs of trust by endorsing it. Websites also exist to facilitate the location of other OpenPGP users to arrange keysignings. The [http://www.gswot.org Gossamer Spider Web of Trust] {{dead link|date=September 2024}} also makes key verification easier by linking OpenPGP users via a hierarchical style web of trust where end users can benefit by coincidental or determined trust of someone who is endorsed as an introducer, or by explicitly trusting GSWoT's top-level key minimally as a level 2 introducer (the top-level key endorses level 1 introducers). |
||
| ⚫ | |||
| ⚫ | {{quotation|As time goes on, you will accumulate keys from other people that you may want to designate as trusted introducers. |
||
| ⚫ | The possibility of finding chains of certificates is often justified by the "[[small world phenomenon]]": given two individuals, it is often possible to find a short chain of people between them such that each person in the chain knows the preceding and following links. However, such a chain is not necessarily useful: the person encrypting an email or verifying a signature not only has to find a chain of signatures from their private key to their correspondent's, but also to trust each person of the chain to be honest and competent about signing keys (that is, they have to judge whether these people are likely to honestly follow the guidelines about verifying the identity of people before signing keys). This is a much stronger constraint. |
||
| ⚫ | |||
| ⚫ | All OpenPGP-compliant implementations include a certificate [[vetting]] scheme to assist with this; its operation has been termed a web of trust. OpenPGP |
||
Another obstacle is the requirement to physically meet with someone (for example, at a [[key signing party]]) to verify their identity and ownership of a public key and email address, which may involve travel expenses and scheduling constraints affecting both sides. A software user may need to verify hundreds of software components produced by thousands of developers located around the world. As the general population of software users cannot meet in person with all software developers to establish direct trust, they must instead rely on the comparatively slower propagation of indirect trust.{{citation needed|date=January 2018}} |
|||
| ⚫ | OpenPGP-compliant implementations also include a vote counting scheme which can be used to determine which public key |
||
Obtaining the PGP/GPG key of an author (or developer, publisher, etc.) from a public key server also presents risks, since the key server is a third-party [[Man-in-the-middle attack|middle-man]], itself vulnerable to abuse or attacks. To avoid this risk, an author can instead choose to publish their public key on their own key server (i.e., a web server accessible through a domain name owned by them, and securely located in their private office or home) and require the use of HKPS-encrypted connections for the transmission of their public key. For details, see [[#WOT assisting solutions|WOT Assisting Solutions]] below. |
|||
| ⚫ | The scheme is flexible, unlike most public key infrastructure designs, and leaves trust |
||
== Strong set == |
|||
| ⚫ | |||
The '''strong set''' refers to the largest collection of [[strongly connected]] [[OpenPGP|PGP]] keys.<ref>{{cite web|url=https://people.apache.org/~henkp/trust/|access-date=13 December 2013|last=Penning|first=Henk|archive-url=https://web.archive.org/web/20130302032948/http://people.apache.org/~henkp/trust/|archive-date=2 March 2013|title=on the apache.org web of trust|url-status=live}}</ref> This forms the basis for the global web of trust. Any two keys in the strong set have a path between them; while islands of sets of keys that only sign each other in a disconnected group can and do exist, only one member of that group needs to exchange signatures with the strong set for that group to also become a part of the strong set.<ref>{{cite web|url=http://dtype.org/keyanalyze/explanation.php|archive-url=https://web.archive.org/web/20090203235946/http://dtype.org/keyanalyze/explanation.php|archive-date=3 February 2009|last=Streib|first=M. Drew|access-date=13 December 2013|title=Explanation of this Keyring Analysis|url-status=dead}}</ref> The strong set had a size of about 55000 Keys at the beginning of the year 2015.<ref>{{cite web|url=http://pgp.cs.uu.nl/plot/|last=Penning|first=Henk P.|access-date=8 January 2015|title=analysis of the strong set in the PGP web of trust}}</ref> |
|||
| ⚫ | |||
| ⚫ | |||
| ⚫ | |||
| ⚫ | |||
| ⚫ | |||
| ⚫ | |||
==Web of trust problems== |
|||
| ⚫ | The OpenPGP web of trust is essentially unaffected by such things as company failures, and has continued to function with little change. However, a related problem does occur |
||
| ⚫ | |||
| ⚫ | A non-technical, social difficulty with a Web of Trust like the one built into PGP/OpenPGP type systems is that every web of trust without a central controller (e.g., a [[Certificate authority|CA]]) depends on other users for trust. Those with new certificates (i.e., produced in the process of generating a new key pair) will not likely be readily trusted by other users' systems, that is by those they have not personally met, until they find enough endorsements for the new certificate. This is because many other Web of Trust users will have their certificate vetting set to require one or more fully trusted endorsers of an otherwise unknown certificate (or perhaps several partial endorsers) before using the public key in that certificate to prepare messages, believe signatures, etc. |
||
==WOT assisting solutions== |
|||
| ⚫ | Despite the wide use of OpenPGP compliant systems and easy availability of on-line multiple [[key server (cryptographic)|key server]]s, it is possible in practice to be unable to readily find someone (or several people) to endorse a new certificate (e.g., by comparing physical identification to key owner information and then digitally signing the new certificate). Users in remote areas or undeveloped ones, for instance, may find other users scarce. And, if the other's certificate is also new (and with no or few endorsements from others), then its signature on any new certificate can offer only marginal benefit toward becoming trusted by still other parties' systems and so able to securely exchange messages with them. [[Key signing party|Key signing parties]] are a relatively popular mechanism to resolve this problem of finding other users who can install one's certificate in existing webs of trust by endorsing it. Websites also exist to facilitate the location of other OpenPGP users to arrange keysignings. The [http://www.gswot.org Gossamer Spider Web of Trust] also makes key verification easier by linking OpenPGP users via a hierarchical style web of trust where end users can benefit by coincidental or determined trust of someone who is endorsed as an introducer, or by explicitly trusting GSWoT's top-level key minimally as a level 2 introducer (the top-level key endorses level 1 introducers). |
||
{{Original research|section|date=April 2024}} |
|||
Physically meeting with original developer or author, is always the best way to obtain and distribute and verify and trust PGP/GPG Keys with highest trust level, and will remain as the best level of best trustworthy way. Publishing of GPG/PGP full Key or full Key fingerprint on/with widely known (physical/paper-material based) book, by the original author/developer, is the 2nd best form of sharing trustworthy key with and for users. Before meeting a developer or author, users should research on their own on the developer or author in book library and via internet, and aware of developer's or author's photo, work, pub-key fingerprint, email-address, etc. |
|||
However, it is not practical for millions of users who want to communicate or message securely to physically meet with each recipient users, and it is also not practical for millions of software users who need to physically meet with hundreds of software developers or authors, whose software or file signing [[Pretty Good Privacy|PGP]]/[[GNU Privacy Guard|GPG]] public Key they want to verify and trust and ultimately use in their computers. Therefore, one or more [[Trusted third party|trusted third-party authority]] (TTPA) type of entity or group need to be available for users and be usable by users, and such entity/group need to be capable of providing trusted-[[Authentication#Digital authentication|verification]] or trust-[[Delegation (computer security)|delegation]] services for millions of users around the world, at any time. |
|||
| ⚫ | The possibility of finding chains of certificates is often justified by the "[[small world phenomenon]]": given two individuals, it is often possible to find a short chain of people between them such that each person in the chain knows the preceding and following links. However, such a chain is not necessarily useful: the person encrypting an email or verifying a signature not only has to find a chain of signatures from |
||
Practically, to verify any downloaded or received content or data or email or file's [[Message authentication|authenticity]], a user need to verify their downloaded main content or main data/email or main file's PGP/GPG [[Digital signature|signature]] code/file (ASC, SIG). So users would need to use original developer's or original author's trustworthy and verified public-key, or users would need to use trustworthy file-signing public-key trusted-by the original owner of that public-key. And to really trust a specific PGP/GPG key, users would need to physically meet with every specific original author or developer, or users would need to physically meet with the original-releaser of file-signing pub-key, or, users would need to find another alternative trustworthy user, who is in trusted-chain of WOT (aka, another user or another developer or another author, who is trusted by that very specific original author or developer), and then physically meet with that person, to verify their real ID with his/her PGP/GPG key (and also provide your own ID and key to the other user, so that both side can sign/certify and trust each other's PGP/GPG key). Whether a software is popular or not, software users are usually located around the world in different locations. It is physically not possible for an original author or developer or file-releaser to provide public-key or trust or ID verification services to millions of users. Neither is it practical for millions of software users to physically meet with each and every software or every software-library or every piece of code's developer or author or releaser, which they will (use or) need to use in their computers. Even with multiple trusted people/person (by original-author) in trusted-chain from WOT, its still not physically or practically possible for every developer or author to meet with every other users, and it is also not possible for every users to meet with hundreds of developers whose software they will be using or working on. When this decentralized hierarchy based WoT chain model will become popular and used by most nearby users, only then physical meeting and pub-key certify and sign procedure of WoT will be easier. |
|||
==Doing the math== |
|||
A few '''solutions''' are: original author/developer need to first set a trust-level to sign/certify their own file-signing key. Then updated public-keys and updated file-signing public-keys must also have to be published and distributed (or made accessible) to users, via online secure and encrypted mediums, so that any user from any location in world, can get the correct and trusted and unmodified public-key. To make sure that each users are getting the correct and trusted public-keys and signed-code/file, original dev/author or original-releaser must publish their updated public-keys on their own [[Key server (cryptographic)|key server]] and force HKPS encrypted connection usage, or publish their updated and full public-keys (and signed-code/file) on their own [[HTTPS]] encrypted webpage, under their own web server, from their own primary domain website, (not-from any sub-domains which are located in external-servers, not-from any mirror, not-from any external/shared forum/wiki etc website servers, not-from any public or external/shared cloud or hosting service servers), and must have to be located and kept securely inside their own premises: own-home, own-home-office, or own-office. In that way, those small pieces of original keys/code, will travel intact through internet and will remain unmodified during transit (because of encrypted connection) and will reach destination without being eavesdropped or modified, into user's side, and can be treated as trustworthy public-keys because of single or multi channel TTPA based verification. When a public-key is obtained (from original developer's own web-server) via more than one [[Trusted third party|TTPA]] (trusted third party authority) based secured, verified and encrypted connection, then it is more trustworthy. |
|||
The work of Audun Jøsang is an algebraic treatment of trust measurements and methods and calculation that attempts to capture how trust varies as it "traverses" a web of trust. The other sites (below) contains a link to his publications. |
|||
A good one to start with might be "[http://www.unik.no/people/josang/papers/Jos1999-NDSS.pdf An Algebra for Assessing Trust in Certification Chains]". Also see [[Subjective logic]] and [[Trust metric]]. |
|||
When original public-keys/signed-codes are shown in original dev's or author's own web server or key server, over encrypted connection or encrypted webpage, then any other files, data or content can be transferred over any type of non-encrypted connection, like: HTTP/FTP etc from any sub-domain server or from any mirror or from any shared cloud/hosting servers, because, non-encrypted connection based downloaded items/data/files can be authenticated later, by using the original public-keys/signed-codes, which were obtained from the original author's/developer's own server over secured, encrypted, and trusted (aka, verified) connection/channels. |
|||
| ⚫ | |||
| ⚫ | |||
Using encrypted connection to transfer keys or signed/signature code/files, allow software users to delegate their trust with a [[Public-key cryptography|PKI]] [[Trusted third party|TTPA]] (trusted third party authority), like public [[Certificate authority|CA]] (Certificate Authority), to help in providing trusted connection in between the original developer/author's web server, and millions of worldwide users' computers, at any time. |
|||
| ⚫ | |||
When the original author/developer's domain-name and name-server is signed by [[Domain Name System Security Extensions|DNSSEC]], and when used [[Transport Layer Security|SSL/TLS]] public certificate is declared/shown in TLSA/[[DNS-based Authentication of Named Entities|DANE]] DNSSec DNS resource-record, (and when SSL/TLS Certs in the trust chain are pinned and used via [[HTTP Public Key Pinning|HPKP]] technique by web servers), then a web-server's webpage or data can also be verified via another PKI [[Trusted third party|TTPA]]: DNSSEC and DNS namespace maintainer [[ICANN]], other than a public CA. DNSSEC is another form of PGP/GPG WOT but for name-servers; it creates a trusted-chain for name-servers first (instead of people/person), and then people/person's PGP/GPG Keys and fingerprints can also be added into a server's DNSSEC DNS records. So any users who want to communicate securely (or any software users), can effectively get/receive their data/key/code/webpage etc. verified (aka, authenticated) via two (aka, dual/double) trusted PKI TTPAs/Channels at the same time: ICANN (DNSSEC) and [[Certificate authority|CA]] ([[Public key certificate|SSL/TLS Certificate]]). So PGP/GPG key/signed-code data (or file) can be trusted, when such solutions and techniques are used: HKPS, HKPS+DNSSEC+DANE, HTTPS, HTTPS+HPKP or HTTPS+HPKP+DNSSEC+DANE. |
|||
Drew Streib wrote the following in his explanation of keyring analysis:<ref>{{cite web|url=http://dtype.org/keyanalyze/explanation.php|archiveurl=https://web.archive.org/web/20090203235946/http://dtype.org/keyanalyze/explanation.php|archivedate=3 February 2009|last=Streib|first=M. Drew|accessdate=13 December 2013|title=Explanation of this Keyring Analysis}}</ref> |
|||
If a vast number of user's group create their own new [[Domain Name System Security Extensions#DNSSEC Lookaside Validation - historical|DLV]] based DNSSEC [[Domain name registry|registry]], and if users use that new DLV (along with ICANN-DNSSEC) root-key in their own local DNSSEC-based DNS Resolver/Server, and if domain-owners also use it for additional signing of their own domain-names, then there can be a new third TTPA. In such case, any PGP/GPG Key/signed-code data or a webpage or web data can be three/triple-channel verified. [[Internet Systems Consortium|ISC]]'s DLV itself can be used as a third TTPA as its still used widely and active, so availability of another new DLV will become fourth TTPA. |
|||
{{quote|There are a variety of metrics one could apply to this set, but I've chosen initially to measure the "mean shortest distance" (MSD) to each key. Since every key is reachable from every other in the strong set, it is possible to find out the shortest distance (number of hops) to any given key from any other key. Averaging these distances gives the MSD to that key from every other key in the strong set. |
|||
| ⚫ | |||
It is desirable to have as short as possible an MSD to your key, as that means that on average, people can reach your key quickly through signatures, and thus your key is relatively more trusted than a key with a higher MSD. |
|||
| ⚫ | |||
NOTE: This does not mean that you should universally trust keys with a low MSD. This is merely a relative measurement for statistical purposes. |
|||
* [[Self-sovereign identity]] |
|||
The MSD has the property of being no more than 1 higher than your lowest signature. In the worst case, every key in the strong set could reach you by getting to that key, plus 1 hop to get to you. It also encourages the joining of keys that are separated by great distances in the graph, as it will make you a highway of sorts for shortest paths between keys in those groups. In the end, it encourages an overall tightening of the world graph, shortening distances between key owners.}} |
|||
| ⚫ | |||
| ⚫ | |||
{{Portal|Cryptography}} |
|||
* [[Global Trust Center]] |
|||
* [[Virtual community]] |
* [[Virtual community]] |
||
* [[Chain of trust]] |
|||
* [[CAcert]] signs OpenPGP keys if you are checked through a web of trust, they also issue free X.509 certificates. |
|||
* [[Root of trust]] |
|||
* [[Thawte]] stopped signing OpenPGP keys many years ago and now only issues X.509 certificates. |
|||
| ⚫ | |||
==References== |
==References== |
||
{{reflist}} |
{{reflist}} |
||
==Further reading== |
|||
{{cite book |
*{{cite book |
||
| last = Ferguson |
| last = Ferguson |
||
| first = Niels |
| first = Niels |
||
| |
| author-link = Niels Ferguson |
||
| |
|author2=Bruce Schneier |
||
| title = Practical Cryptography |
| title = Practical Cryptography |
||
| publisher = [[John Wiley & Sons]] |
| publisher = [[John Wiley & Sons]] |
||
| year = 2003 |
| year = 2003 |
||
| Line 90: | Line 96: | ||
==External links== |
==External links== |
||
*[http://www.rubin.ch/pgp/weboftrust.en.html An explanation of the PGP Web of Trust] |
*[http://www.rubin.ch/pgp/weboftrust.en.html An explanation of the PGP Web of Trust] |
||
*[https://web.archive.org/web/20200806172139/https://pgp.cs.uu.nl/plot/ Analysis of the ''strong set'' in the PGP web of trust], no longer maintained; last archived link from August 2020. |
|||
*[http://www.wim.uni-koeln.de/uploads/media/The_PGP_Trust_Model.pdf "The PGP Trust Model"] - by Alfarez Abdul-Rahman |
|||
*[http://pgp.cs.uu.nl/plot/ analysis of the ''strong set'' in the PGP web of trust] - regularly updated |
|||
{{Cryptography navbox | public-key}} |
{{Cryptography navbox | public-key}} |
||
| Line 97: | Line 102: | ||
{{DEFAULTSORT:Web Of Trust}} |
{{DEFAULTSORT:Web Of Trust}} |
||
[[Category:Key management]] |
[[Category:Key management]] |
||
[[Category:Public |
[[Category:Public key infrastructure]] |
||
[[Category: |
[[Category:OpenPGP]] |
||
[[Category: |
[[Category:Authentication]] |
||
[[Category: |
[[Category:Computational trust]] |
||
[[Category:Identity management]] |
|||
[[ja:公開鍵基盤#信用の輪(Web of Trust)]] |
[[ja:公開鍵基盤#信用の輪(Web of Trust)]] |
||
Latest revision as of 16:05, 29 September 2024
This article needs additional citations for verification. (May 2023) |

In cryptography, a web of trust is a concept used in PGP, GnuPG, and other OpenPGP-compatible systems to establish the authenticity of the binding between a public key and its owner. Its decentralized trust model is an alternative to the centralized trust model of a public key infrastructure (PKI), which relies exclusively on a certificate authority (or a hierarchy of such).[1] As with computer networks, there are many independent webs of trust, and any user (through their public key certificate) can be a part of, and a link between, multiple webs.
The web of trust concept was first put forth by PGP creator Phil Zimmermann in 1992 in the manual for PGP version 2.0:
As time goes on, you will accumulate keys from other people that you may want to designate as trusted introducers. Everyone else will each choose their own trusted introducers. And everyone will gradually accumulate and distribute with their key a collection of certifying signatures from other people, with the expectation that anyone receiving it will trust at least one or two of the signatures. This will cause the emergence of a decentralized fault-tolerant web of confidence for all public keys.
Note the use of the word emergence in this context. The web of trust makes use of the concept of emergence.
Operation of a web of trust
[edit]All OpenPGP-compliant implementations include a certificate vetting scheme to assist with this; its operation has been termed a web of trust. OpenPGP certificates (which include one or more public keys along with owner information) can be digitally signed by other users who, by that act, endorse the association of that public key with the person or entity listed in the certificate. This is commonly done at key signing parties.[2]
OpenPGP-compliant implementations also include a vote counting scheme which can be used to determine which public key – owner association a user will trust while using PGP. For instance, if three partially trusted endorsers have vouched for a certificate (and so its included public key – owner binding), or if one fully trusted endorser has done so, the association between owner and public key in that certificate will be trusted to be correct. The parameters are user-adjustable (e.g., no partials at all, or perhaps six partials) and can be completely bypassed if desired.
The scheme is flexible, unlike most public key infrastructure designs, and leaves trust decisions in the hands of individual users. It is not perfect and requires both caution and intelligent supervision by users. Essentially all PKI designs are less flexible and require users to follow the trust endorsement of the PKI generated, certificate authority (CA)-signed, certificates.
Simplified explanation
[edit]There are two keys pertaining to a person: a public key which is shared openly and a private key that is withheld by the owner. The owner's private key will decrypt any information encrypted with its public key. In the web of trust, each user has a key ring with other people's public keys.
Senders encrypt their information with the recipient's public key, and only the recipient's private key will decrypt it. Each sender then digitally signs the encrypted information with their private key. When the recipient verifies the received encrypted information against the sender's public key, they can confirm that it is from the sender. Doing this will ensure that the encrypted information came from the specific user and has not been tampered with, and only the intended recipient can decrypt the information (because only they know their private key).
Contrast with typical PKI
[edit]Unlike WOT, a typical X.509 PKI enables each certificate to be signed by a single party: a certificate authority (CA). The CA's certificate may itself be signed by a different CA, all the way up to a 'self-signed' root certificate. Root certificates must be available to those who use a lower-level CA certificate and so are typically distributed widely. They are for instance, distributed with such applications as browsers and email clients. In this way SSL/TLS-protected Web pages, email messages, etc. can be authenticated without requiring users to manually install root certificates. Applications commonly include over one hundred root certificates from dozens of PKIs, thus by default bestowing trust throughout the hierarchy of certificates which lead back to them.
WOT favors the decentralization of trust anchors to prevent a single point of failure from compromising the CA hierarchy.[3]
Problems
[edit]Loss of private keys
[edit]The OpenPGP web of trust is essentially unaffected by such things as company failures, and has continued to function with little change. However, a related problem does occur: users, whether individuals or organizations, who lose track of a private key can no longer decrypt messages sent to them produced using the matching public key found in an OpenPGP certificate. Early PGP certificates did not include expiry dates, and those certificates had unlimited lives. Users had to prepare a signed cancellation certificate against the time when the matching private key was lost or compromised. One very prominent cryptographer is still getting messages encrypted using a public key for which he long ago lost track of the private key.[4] They can't do much with those messages except discard them after notifying the sender that they were unreadable and requesting resending with a public key for which they still have the matching private key. Later PGP, and all OpenPGP compliant certificates include expiry dates which automatically preclude such troubles (eventually) when used sensibly. This problem can also be easily avoided by the use of "designated revokers", which were introduced in the early 1990s. A key owner may designate a third party that has permission to revoke the key owner's key (in case the key owner loses his own private key and thus loses the ability to revoke his own public key).
Public key authenticity check
[edit]A non-technical, social difficulty with a Web of Trust like the one built into PGP/OpenPGP type systems is that every web of trust without a central controller (e.g., a CA) depends on other users for trust. Those with new certificates (i.e., produced in the process of generating a new key pair) will not likely be readily trusted by other users' systems, that is by those they have not personally met, until they find enough endorsements for the new certificate. This is because many other Web of Trust users will have their certificate vetting set to require one or more fully trusted endorsers of an otherwise unknown certificate (or perhaps several partial endorsers) before using the public key in that certificate to prepare messages, believe signatures, etc.
Despite the wide use of OpenPGP compliant systems and easy availability of on-line multiple key servers, it is possible in practice to be unable to readily find someone (or several people) to endorse a new certificate (e.g., by comparing physical identification to key owner information and then digitally signing the new certificate). Users in remote areas or undeveloped ones, for instance, may find other users scarce. And, if the other's certificate is also new (and with no or few endorsements from others), then its signature on any new certificate can offer only marginal benefit toward becoming trusted by still other parties' systems and so able to securely exchange messages with them. Key signing parties are a relatively popular mechanism to resolve this problem of finding other users who can install one's certificate in existing webs of trust by endorsing it. Websites also exist to facilitate the location of other OpenPGP users to arrange keysignings. The Gossamer Spider Web of Trust [dead link] also makes key verification easier by linking OpenPGP users via a hierarchical style web of trust where end users can benefit by coincidental or determined trust of someone who is endorsed as an introducer, or by explicitly trusting GSWoT's top-level key minimally as a level 2 introducer (the top-level key endorses level 1 introducers).
The possibility of finding chains of certificates is often justified by the "small world phenomenon": given two individuals, it is often possible to find a short chain of people between them such that each person in the chain knows the preceding and following links. However, such a chain is not necessarily useful: the person encrypting an email or verifying a signature not only has to find a chain of signatures from their private key to their correspondent's, but also to trust each person of the chain to be honest and competent about signing keys (that is, they have to judge whether these people are likely to honestly follow the guidelines about verifying the identity of people before signing keys). This is a much stronger constraint.
Another obstacle is the requirement to physically meet with someone (for example, at a key signing party) to verify their identity and ownership of a public key and email address, which may involve travel expenses and scheduling constraints affecting both sides. A software user may need to verify hundreds of software components produced by thousands of developers located around the world. As the general population of software users cannot meet in person with all software developers to establish direct trust, they must instead rely on the comparatively slower propagation of indirect trust.[citation needed]
Obtaining the PGP/GPG key of an author (or developer, publisher, etc.) from a public key server also presents risks, since the key server is a third-party middle-man, itself vulnerable to abuse or attacks. To avoid this risk, an author can instead choose to publish their public key on their own key server (i.e., a web server accessible through a domain name owned by them, and securely located in their private office or home) and require the use of HKPS-encrypted connections for the transmission of their public key. For details, see WOT Assisting Solutions below.
Strong set
[edit]The strong set refers to the largest collection of strongly connected PGP keys.[5] This forms the basis for the global web of trust. Any two keys in the strong set have a path between them; while islands of sets of keys that only sign each other in a disconnected group can and do exist, only one member of that group needs to exchange signatures with the strong set for that group to also become a part of the strong set.[6] The strong set had a size of about 55000 Keys at the beginning of the year 2015.[7]
Mean shortest distance
[edit]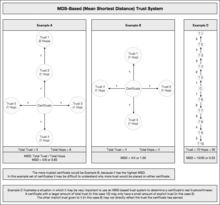
In statistical analysis of the PGP/GnuPG/OpenPGP Web of trust the mean shortest distance (MSD) is one measurement of how "trusted" a given PGP key is within the strongly connected set of PGP keys that make up the Web of trust.
MSD has become a common metric for analysis of sets of PGP keys. Very often you will see the MSD being calculated for a given subset of keys and compared with the global MSD which generally refers to the keys ranking within one of the larger key analyses of the global Web of trust.
WOT assisting solutions
[edit]This section possibly contains original research. (April 2024) |
Physically meeting with original developer or author, is always the best way to obtain and distribute and verify and trust PGP/GPG Keys with highest trust level, and will remain as the best level of best trustworthy way. Publishing of GPG/PGP full Key or full Key fingerprint on/with widely known (physical/paper-material based) book, by the original author/developer, is the 2nd best form of sharing trustworthy key with and for users. Before meeting a developer or author, users should research on their own on the developer or author in book library and via internet, and aware of developer's or author's photo, work, pub-key fingerprint, email-address, etc.
However, it is not practical for millions of users who want to communicate or message securely to physically meet with each recipient users, and it is also not practical for millions of software users who need to physically meet with hundreds of software developers or authors, whose software or file signing PGP/GPG public Key they want to verify and trust and ultimately use in their computers. Therefore, one or more trusted third-party authority (TTPA) type of entity or group need to be available for users and be usable by users, and such entity/group need to be capable of providing trusted-verification or trust-delegation services for millions of users around the world, at any time.
Practically, to verify any downloaded or received content or data or email or file's authenticity, a user need to verify their downloaded main content or main data/email or main file's PGP/GPG signature code/file (ASC, SIG). So users would need to use original developer's or original author's trustworthy and verified public-key, or users would need to use trustworthy file-signing public-key trusted-by the original owner of that public-key. And to really trust a specific PGP/GPG key, users would need to physically meet with every specific original author or developer, or users would need to physically meet with the original-releaser of file-signing pub-key, or, users would need to find another alternative trustworthy user, who is in trusted-chain of WOT (aka, another user or another developer or another author, who is trusted by that very specific original author or developer), and then physically meet with that person, to verify their real ID with his/her PGP/GPG key (and also provide your own ID and key to the other user, so that both side can sign/certify and trust each other's PGP/GPG key). Whether a software is popular or not, software users are usually located around the world in different locations. It is physically not possible for an original author or developer or file-releaser to provide public-key or trust or ID verification services to millions of users. Neither is it practical for millions of software users to physically meet with each and every software or every software-library or every piece of code's developer or author or releaser, which they will (use or) need to use in their computers. Even with multiple trusted people/person (by original-author) in trusted-chain from WOT, its still not physically or practically possible for every developer or author to meet with every other users, and it is also not possible for every users to meet with hundreds of developers whose software they will be using or working on. When this decentralized hierarchy based WoT chain model will become popular and used by most nearby users, only then physical meeting and pub-key certify and sign procedure of WoT will be easier.
A few solutions are: original author/developer need to first set a trust-level to sign/certify their own file-signing key. Then updated public-keys and updated file-signing public-keys must also have to be published and distributed (or made accessible) to users, via online secure and encrypted mediums, so that any user from any location in world, can get the correct and trusted and unmodified public-key. To make sure that each users are getting the correct and trusted public-keys and signed-code/file, original dev/author or original-releaser must publish their updated public-keys on their own key server and force HKPS encrypted connection usage, or publish their updated and full public-keys (and signed-code/file) on their own HTTPS encrypted webpage, under their own web server, from their own primary domain website, (not-from any sub-domains which are located in external-servers, not-from any mirror, not-from any external/shared forum/wiki etc website servers, not-from any public or external/shared cloud or hosting service servers), and must have to be located and kept securely inside their own premises: own-home, own-home-office, or own-office. In that way, those small pieces of original keys/code, will travel intact through internet and will remain unmodified during transit (because of encrypted connection) and will reach destination without being eavesdropped or modified, into user's side, and can be treated as trustworthy public-keys because of single or multi channel TTPA based verification. When a public-key is obtained (from original developer's own web-server) via more than one TTPA (trusted third party authority) based secured, verified and encrypted connection, then it is more trustworthy.
When original public-keys/signed-codes are shown in original dev's or author's own web server or key server, over encrypted connection or encrypted webpage, then any other files, data or content can be transferred over any type of non-encrypted connection, like: HTTP/FTP etc from any sub-domain server or from any mirror or from any shared cloud/hosting servers, because, non-encrypted connection based downloaded items/data/files can be authenticated later, by using the original public-keys/signed-codes, which were obtained from the original author's/developer's own server over secured, encrypted, and trusted (aka, verified) connection/channels.
Using encrypted connection to transfer keys or signed/signature code/files, allow software users to delegate their trust with a PKI TTPA (trusted third party authority), like public CA (Certificate Authority), to help in providing trusted connection in between the original developer/author's web server, and millions of worldwide users' computers, at any time.
When the original author/developer's domain-name and name-server is signed by DNSSEC, and when used SSL/TLS public certificate is declared/shown in TLSA/DANE DNSSec DNS resource-record, (and when SSL/TLS Certs in the trust chain are pinned and used via HPKP technique by web servers), then a web-server's webpage or data can also be verified via another PKI TTPA: DNSSEC and DNS namespace maintainer ICANN, other than a public CA. DNSSEC is another form of PGP/GPG WOT but for name-servers; it creates a trusted-chain for name-servers first (instead of people/person), and then people/person's PGP/GPG Keys and fingerprints can also be added into a server's DNSSEC DNS records. So any users who want to communicate securely (or any software users), can effectively get/receive their data/key/code/webpage etc. verified (aka, authenticated) via two (aka, dual/double) trusted PKI TTPAs/Channels at the same time: ICANN (DNSSEC) and CA (SSL/TLS Certificate). So PGP/GPG key/signed-code data (or file) can be trusted, when such solutions and techniques are used: HKPS, HKPS+DNSSEC+DANE, HTTPS, HTTPS+HPKP or HTTPS+HPKP+DNSSEC+DANE.
If a vast number of user's group create their own new DLV based DNSSEC registry, and if users use that new DLV (along with ICANN-DNSSEC) root-key in their own local DNSSEC-based DNS Resolver/Server, and if domain-owners also use it for additional signing of their own domain-names, then there can be a new third TTPA. In such case, any PGP/GPG Key/signed-code data or a webpage or web data can be three/triple-channel verified. ISC's DLV itself can be used as a third TTPA as its still used widely and active, so availability of another new DLV will become fourth TTPA.
See also
[edit]- Friend-to-friend (F2F) computer network.
- Self-sovereign identity
- Virtual community
- Chain of trust
- Root of trust
References
[edit]- ^ Chien, Hung-Yu (2021-08-19). "Dynamic Public Key Certificates with Forward Secrecy". Electronics. 10 (16): 2009. doi:10.3390/electronics10162009. ISSN 2079-9292.
- ^ Ulrich, Alexander; Holz, Ralph; Hauck, Peter; Carle, Georg (2011). "Investigating the OpenPGP Web of Trust". In Atluri, Vijay; Diaz, Claudia (eds.). Computer Security – ESORICS 2011. Lecture Notes in Computer Science. Vol. 6879. Berlin, Heidelberg: Springer. pp. 489–507. doi:10.1007/978-3-642-23822-2_27. ISBN 978-3-642-23822-2.
- ^ Nightingale, Johnathan. "Fraudulent *.google.com Certificate". Retrieved 29 August 2011.
- ^ Ferguson, Niels; Schneier, Bruce (2003). Practical Cryptography. Wiley. p. 333. ISBN 978-0471223573.
Bruce lost a PGP key almost a decade ago; he still gets email encrypted with the corresponding certificate.
- ^ Penning, Henk. "on the apache.org web of trust". Archived from the original on 2 March 2013. Retrieved 13 December 2013.
- ^ Streib, M. Drew. "Explanation of this Keyring Analysis". Archived from the original on 3 February 2009. Retrieved 13 December 2013.
- ^ Penning, Henk P. "analysis of the strong set in the PGP web of trust". Retrieved 8 January 2015.
Further reading
[edit]- Ferguson, Niels; Bruce Schneier (2003). Practical Cryptography. John Wiley & Sons. ISBN 0-471-22357-3.
External links
[edit]- An explanation of the PGP Web of Trust
- Analysis of the strong set in the PGP web of trust, no longer maintained; last archived link from August 2020.
