P3P: Difference between revisions
→External links: add {{W3C Standards}} |
|||
| Line 121: | Line 121: | ||
*[http://articles.techrepublic.com.com/5100-10878-1059571.html/ Tech Republic] |
*[http://articles.techrepublic.com.com/5100-10878-1059571.html/ Tech Republic] |
||
*[http://epic.org/ Electronic Privacy Information Center] |
*[http://epic.org/ Electronic Privacy Information Center] |
||
{{W3C Standards}} |
|||
[[Category:World Wide Web]] |
[[Category:World Wide Web]] |
||
Revision as of 09:54, 19 January 2009
The Platform for Privacy Preferences Project, or P3P, is a protocol allowing websites to declare their intended use of information they collect about browsing users. Designed to give users more control of their personal information when browsing, P3P was developed by the World Wide Web Consortium (W3C) and officially recommended on April 16, 2002.
Purpose
As the World Wide Web became a genuine medium in which to sell products and services, electronic commerce websites tried to collect more information about the people who purchased their merchandise. Some companies used controversial practices such as tracker cookies to ascertain the users' demographic information and buying habits, using this information to provide specifically targeted advertisements. Users who saw this as an invasion of privacy would sometimes turn off HTTP cookies or use proxy servers to keep their personal information secure. P3P is designed to give users a more precise control of the kind of information that they allow to release. According to the W3C the main goal of P3P “is to increase user trust and confidence in the Web through technical empowerment.” [1]
P3P is a machine that helps to express a website’s data management practices. P3P manages information through privacy policies. When a website uses P3P they set up a set of policies that allows them to state their intended uses of personal information that may be gathered from their site visitors. When a user decides to use P3P they set their own set of policies and state what personal information they will allow to be seen by the sites that they visit. Then when a user visits a site P3P will compare what personal information the user is willing to release, and what information the server wants to get – if the two do not match, P3P will inform the user and ask if he/she is willing to proceed to the site, and risk giving up more personal information. [2]. As an example, a user may store in the browser preferences that information about their browsing habits should not be collected. If the policy of a Website states that a cookie is used for this purpose, the browser automatically rejects the cookie. The main content of a privacy policy is the following:
- which information the server stores:
- which kind of information is collected (identifying or not);
- which particular information is collected (IP address, email address, name, etc.);
- use of the collected information:
- how this information is used (for regular navigation, tracking, personalization, telemarketing, etc.);
- who will receive this information (only the current company, third party, etc.);
- permanence and visibility:
- how long information is stored;
- whether and how the user can access the stored information (read-only, optin, optout).
The privacy policy can be retrieved as an XML file or can be included, in compact form, in the HTTP header. The location of the XML policy file that applies to a given document can be:
- specified in the HTTP header of the document
- specified in the HTML head of the document
- if none of the above is specified, the well-known location /w3c/p3p.xml is used (for a similar location compare /favicon.ico)
P3P allows to specify a max-age for caching. A dummy /w3c/p3p.xml file could use this feature:
<META xmlns="http://www.w3.org/2002/01/P3Pv1">
<POLICY-REFERENCES>
<EXPIRY max-age="10000000"/><!-- about four months -->
</POLICY-REFERENCES>
</META>
P3P User Agents
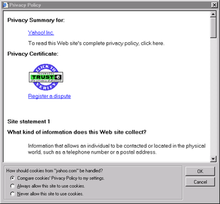
Microsoft Internet Explorer provides the ability to display P3P privacy policies, and compare the P3P policy with your own settings to decide whether or not to allow cookies from a particular site. However, the P3P functionality in Internet Explorer extends only to cookie blocking, and will not alert you to an entire web site that violates your privacy preferences. Users who wish to use a full P3P user agent should use the AT&T Privacy Bird, which is now maintained by Carnegie Mellon's Usable Privacy and Security Laboratory.
The Privacy Finder service was also created by Carnegie Mellon's Usable Privacy and Security Laboratory. It is a publicly available "P3P-enabled search engine." A user can enter a search term along with their stated privacy preferences, and is then presented with a list of search results which are ordered based on whether the sites comply with their preferences. This works by crawling the web and maintaining a P3P cache for every site that ever appears in a search query. The cache is updated every 24 hours so that every policy is guaranteed to be relatively up to date. The service also allows users to quickly determine why a site does not comply with their preferences, as well as allowing them to view a dynamically generated natural language privacy policy based on the P3P data. This is advantageous over simply reading the original natural language privacy policy on a web site because many privacy policies are written in legalese and are extremely convoluted. Additionally, in this case the user does not have to visit the web site to read its privacy policy.
Benefits
P3P allows browsers to understand their privacy policies in a simplified and organized manner rather than searching throughout the entire website. By setting your own privacy settings on a certain level, P3P will automatically block any cookies that you might not want on your computer. Additionally, the World Wide Web Consortium (W3C) explains that P3P will allow browsers to transfer user data to services, ultimately promoting an online sharing community.
Additionally, the P3P Toolbox [3] developed by the Internet Education Foundation recommends, that anyone who is concerned about increasing their users’ trust and privacy should consider implementing P3P. The P3P toolbox site explains how companies have taken individuals data in order to promote new products or services. Furthermore, in recent years companies have taken individuals information and created profiles, which they then market without the individuals consent. Moreover, all this data is misused and we as consumers pay the price and become worrisome of issues such as: junk mail, identity theft and forms of discrimination; therefore implementing P3P's protocol is good and beneficial for internet browsers.
Moreover, since there has been an increase of browsers there are more users at risk running into privacy problems. But the Internet Education Foundation points out that, “P3P has been developed to help steer the force of technology a step further toward automatic communication of data management practices and individual privacy preferences.” [4]
Criticisms
The Electronic Privacy Information Center (EPIC) has been critical of P3P and believes P3P makes it too difficult for users to protect their privacy [5]. Although the EPIC is an advocate for privacy, the center assessed P3P in 2000 and referred to the technology as a “Pretty Poor Policy.” According to the EPIC, some P3P software is too complex and difficult for the average person to understand, and many Internet users are unfamiliar with how to use the default P3P software on their computers or how to install additional P3P software. Another concern is that websites are not obligated to use P3P, and neither are Internet users. P3P has been known to undermine public confidence by collecting enormous amounts of information that can be used against its user. Moreover, the EPIC website points out that P3Ps protocol would become burdensome for the browser and not as beneficial or efficient as it was intended to be.
The basic idea of privacy protection can be misleading to the visitors on the site. For example, people think that their privacy is actually being protected, but it is not. P3P facilitates data collection from websites. If the actual intention of p3p was to protect visitors to web sites then the information gathering would not be so easy to pass along personal information. Also, people who visit websites where p3p is present are uninformed and misunderstand the level of privacy that p3p provides. There needs to be more effective ways of educating people on the level of privacy and what p3p actually does to protect people.
Another main concern is that the data that is collected does not have an expiration date. People who buy something on the internet will have that information saved for an infinite amount of time, whether it will be recorded for a year or ten. This problem has led people to question where their information is being distributed to and for how long third parties will have access to their information. The idea that people’s personal information can be distributed to other people for an indeterminate amount of time makes people very uncomfortable.
A key problem that occurs with the use of P3P is that there is a lack of enforcement. Thus, promises made to users of P3P can go unfulfilled. Though by using P3P a company/website makes a promise of privacy and of the use of gathered data to the site’s users, there are no real legal ramifications if the company decides to use the information for other functions. Currently, there are no actual laws that have been passed by the United States about data protection. Though it would be nice to be able to trust every company that states its use for our information, there is no binding reason that the company must actually adhere to the rules it says it will comply by. Though using P3P technically qualifies as a contract, the lack of federal regulation downplays the need for companies to abide. [6]
The agreement to use P3P not only puts in place unenforceable promises, but it also prolongs the adoption of federal laws that would actually inhibit the access and ability to use private information. If the government were to step in and attempt to protect Internet users with federal laws on what information can be accessed, and specific regulations on how user information can be used, companies wouldn’t maintain the leeway they do now to use information as they please, despite what they may actually tell users. Chris Hoofnagle works for EPIC and he argues that P3P fails to inform its users that it’s a way to avoid government regulation. He says, “We know as a fact that Microsoft is using P3P as a tool to stop federal privacy legislation. They’ll deny it, but I’ve been to meetings where I’ve seen it happen.” [7]
Critics of P3P also argue that non-compliant sites are excluded. According to a study done by CyLab Privacy Interest Group at Carnegie Mellon University [8] only 15% of the top 5,000 websites incorporate P3P. Therefore many sites that don’t include the code but do practice high privacy standards will not be accessible to users who use P3P as their only online privacy guide.
EPIC, the technology's obviously largest critic, also talks about how the development and implementation of P3P can cause a monopoly of private information. Since it tends to be only major companies who implement P3P on their websites, only these major companies are tending to then gather this information seeing as only their privacy policies can compare to privacy preferences of users. The EPIC website says, "The incredible complexity of P3P, combined with the way that popular browsers are likely to implement the protocol would seem to preclude it as a privacy-protective technology," EPIC continues on to state, "Rather, P3P may actually strengthen the monopoly position over personal information that U.S. data marketers now enjoy." [9]
The failure for its immediate adoption can be related to the idea of it being a notice and choice approach that doesn’t comply with the Fair Information Practices. According to the Chairman of the FTC [10] , privacy laws are key in today’s society in order to protect the consumer from providing too much personal information for other’s benefit. Some believe that there should be a limit to the collection and use of the consumer’s personal data online. Currently sites are not required under any United States laws to comply with the privacy policies they publish, therefore P3P casues some controversy with consumers who are concerned about the release of their personal information and are only able to rely on P3P’S protocol to protect their privacy.
As people become comfortable with P3P, the technology may be limiting the perceived need of related privacy legislation.
Michael Kaply from IBM is reported saying the following when the Mozilla Foundation was considering the removal of P3P support from their browser-line [11]
Ah the memories.
We (IBM) wrote the original P3P implementation and then Netscape proceeded to write their own. So both our companies wasted immense amounts of time that everyone thought was a crappy proposal to begin with.
Remove it.
Live Leer, a PR manager for Opera Software explains the deliberate lack of P3P support in their browser[12]
At the moment, we aren't sure whether P3P is the best solution. P3P is among the specifications we are considering for support in the future. There have been some issues with how well P3P will protect privacy, and for that reason we have decided to wait until these are resolved.
Alternatives
P3P user agents are not the only option available for Internet users that want to ensure their privacy. Two of the main alternatives to P3P include anonymous e-mailers and anonymous proxy servers.
Anonymous e-mailers allow Internet users to send safe and secure e-mails by sending and receiving e-mails anonymously [13]. The anonymous e-mailer programs protect e-mail through encryption, the process of transforming information to make it unreadable to anyone without the correct key. Encrypting the e-mail allows the user to send or receive e-mails without being tracked or intercepted by others. There are multiple anonymous e-mailers available. Some anonymous e-mailers encrypt only incoming mail, some encrypt only outgoing mail and others encrypt both. Aderes Security is a program that allows users to send anonymous e-mails and to search the web without revealing their identity [14]. CryptoHeaven allows users to send and receive secure e-mails while remaining anonymous [15]. Both require a paid subscription for their services.
An anonymous proxy servers, or anonymizer, provides safe and secure web browsing for Internet users by hiding the user’s IP address [16]. Every computer is assigned an IP address when it is connected to the Internet. An IP address is essentially a unique ID or address that commercial services and online snoopers can use to track Internet activity and sites users have visited. Anonymous proxy servers can be used to prevent this tracking of personal browsing. There are various tools one can use in order to surf the web anonymously [17]. One tool that allows you to search the web anonymously is called The Anonymizer [18]. The Anonymizer is software that users can install to their personal computers to hide their IP address while they surf the net. Using this program, users surf like they normally would, but their IP address remains private. The Cloak is another anonymous surfing tool that does not require any downloading any software [19]. Instead, users visit The Cloak’s site and click on a button that allows them to begin surfing anonymously. In addition to serving as an anonymous proxy server through an encrypted connection, The Cloak allows users to store remote cookies on its site and filter content based on user preferences.
The main alternative to P3P may not be these technologies, but instead stronger laws to regulate what kind of information from Internet users can be collected and retained by websites. For example, the Data Protection Act of Europe provides individuals with a certain set of principles about how personal information is collected and the person's rights to protecting their personal data [20]. The act allows individuals to control the type of information that is being collected from them. Various principles are included within the act, such the rule that individual has the right to retrieve the data collected about them at any time under certain conditions. Moreover, the individual's personal information cannot be kept longer than necessary, and personal information cannot be released to others unless the individual gives their consent.
Currently, the United States has no federal law protecting the privacy of personal information shared online. However, there are some sectoral laws at the federal and state level that offer some protection for certain types of information collected about individuals [21]. For example, the Fair Credit Reporting Act (FCRA) of 1970 makes it illegal for consumer reporting agencies to disclose personal information only under three specified circumstances: credit, employment or insurance evaluation, government grant or license, or a “legitimate business need” that involves the consumer. The Children's Online Privacy Protection Act (COPPA) of 1998 makes it illegal for online services and commercial sites directed at children to collect personal information about children 12 years and younger without obtaining parental consent. The act also requires online sites to provide parents with information about their privacy practices and to allow parents to review and correct any personal information collected about their children. A list of other sectoral privacy laws in the United States can be viewed at the Consumer Privacy Guide's website.
The Future of p3p
There are many groups who are working to further the future of p3p to make it easier for people to use. Some of these groups are:
Transparent Accountable Datamining Initiative [TAMI] is a group out of MIT’s Computer Science and Artificial Intelligence Laboratory. The goal of TAMI is to create technical, legal, and policy foundations for transparency and accountability in large-scale aggregation. TAMI hopes to help people manage privacy risks in a world where technology is constantly changing.
Policy Aware Web [PAW] is a scalable mechanism for the exchange of rules and proofs for unlimited access control to the Web. “It creates a system of Policy Aware infrastructure using systematic Web rules language with a theorem prover” [22].
See also
External links
- W3C P3P site
- W3C P3P Specifications
- A resource for P3P related tools
- Privacy Bird
- Privacy Finder
- The Privacy Place
- P3P in Internet Explorer 6
- P3PEdit P3P editor/generator
- The price of privacy The Walyou Blog
- Center for Democracy and Technology
- Fair Information Practices In The Electronic Marketplace
- 2006 Privacy Policy Trends Report
- Tech Republic
- Electronic Privacy Information Center
