Sponge function: Difference between revisions
m Missing comma |
m singular |
||
| Line 1: | Line 1: | ||
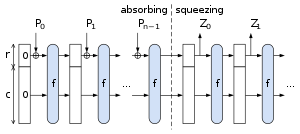
[[Image:SpongeConstruction.svg|thumb|upright=1.35|right|alt=Illustration of the sponge construction |The sponge construction for hash functions. p<sub>i</sub> are blocks of the input string, z<sub>i</sub> are hashed output blocks.]] |
[[Image:SpongeConstruction.svg|thumb|upright=1.35|right|alt=Illustration of the sponge construction |The sponge construction for hash functions. p<sub>i</sub> are blocks of the input string, z<sub>i</sub> are hashed output blocks.]] |
||
In [[cryptography]], a '''sponge function''' or '''sponge construction''' is a class of [[algorithm]]s with finite [[state (computer science)|internal state]] that take an input [[bit stream]] of any length and produce an output bit stream of any desired length. Sponge functions have both theoretical and practical uses. They can be used to model or implement many [[cryptographic primitive]]s, including [[cryptographic hash]]es, [[message authentication codes]], [[mask generation function]]s, [[stream cipher]]s, [[pseudo-random number generator]]s, and [[authenticated encryption]].<ref>{{cite web |url=http://sponge.noekeon.org/SpongeDuplex.pdf |title=Duplexing The Sponge |author=The Keccak Team}}</ref> |
In [[cryptography]], a '''sponge function''' or '''sponge construction''' is any of a class of [[algorithm]]s with finite [[state (computer science)|internal state]] that take an input [[bit stream]] of any length and produce an output bit stream of any desired length. Sponge functions have both theoretical and practical uses. They can be used to model or implement many [[cryptographic primitive]]s, including [[cryptographic hash]]es, [[message authentication codes]], [[mask generation function]]s, [[stream cipher]]s, [[pseudo-random number generator]]s, and [[authenticated encryption]].<ref>{{cite web |url=http://sponge.noekeon.org/SpongeDuplex.pdf |title=Duplexing The Sponge |author=The Keccak Team}}</ref> |
||
==Construction== |
==Construction== |
||
Revision as of 15:02, 2 October 2018
In cryptography, a sponge function or sponge construction is any of a class of algorithms with finite internal state that take an input bit stream of any length and produce an output bit stream of any desired length. Sponge functions have both theoretical and practical uses. They can be used to model or implement many cryptographic primitives, including cryptographic hashes, message authentication codes, mask generation functions, stream ciphers, pseudo-random number generators, and authenticated encryption.[1]
Construction
A sponge function is built from three components:[2]
- a state memory, S, containing b bits,
- a function that transforms the state memory (often it is a pseudorandom permutation of the state values)
- a padding function P
The state memory is divided into two sections: one of size r (the bitrate) and the remaining part of size c (the capacity). These sections are denoted R and C respectively.
The padding function appends enough bits to the input string so that the length of the padded input is a whole multiple of the bitrate, r. The padded input can thus be broken into r-bit blocks.
Operation
The sponge function operates as follows:
- The state S is initialized to zero
- The input string is padded. This means the input is transformed into blocks of r bits using the padding function P.
- for each r-bit block B of the padded input:
- R is replaced with R XOR B (using bitwise XOR)
- S is replaced by f(S)
This process "absorbs" (in the sponge metaphor) all blocks of the padded input string.
The sponge function output is now ready to be produced ("squeezed out") as follows:
- the R portion of the state memory is output
- repeat until enough bits are output:
- S is replaced by f(S)
- the R portion of the state memory is output
If less than r bit remain to be output, then R will be truncated (only part of R will be output).
Another metaphor describes the state memory as an "entropy pool", with input "poured into" the pool, and the transformation function referred to as "stirring the entropy pool".[3]
Note that input bits are never XORed into the C portion of the state memory, nor are any bits of C ever output directly. The extent to which C is altered by the input depends entirely on the transformation function f. In hash applications, resistance to collision or preimage attacks depends on C, and its size (the "capacity" c) is typically twice the desired resistance level.
Duplex construction
It is also possible to absorb and squeeze in an alternating fashion.[4] This operation is called the duplex construction or duplexing. It can be the basis of a single pass authenticated encryption system.
- The state S is initialized to zero
- R is XORed with the first r-bit block of the input
- S is replaced by f(S)
- R is now the first r bits of the output.
- R is XORed with the next r-bit block of the input
- S is replaced by f(S)
- R is now the next r bits of the output.
- …
Overwrite mode
It is possible to omit the XOR operations during absorption, while still maintaining the chosen security level.[4] In this mode, in the absorbing phase, the next block of the input overwrites the R part of the state. This allows keeping a smaller state between the steps. Since the R part will be overwritten anyway, it can be discarded in advance, only the C part must be kept.
Applications
Sponge functions have both theoretical and practical uses. In theoretical cryptanalysis, a random sponge function is a sponge construction where f is a random permutation or transformation, as appropriate. Random sponge functions capture more of the practical limitations of cryptographic primitives than does the widely used random oracle model, in particular the finite internal state.[5]
The sponge construction can also be used to build practical cryptographic primitives. For example, Keccak cryptographic sponge with a 1600-bit state has been selected by NIST as the winner in the SHA-3 competition. The strength of Keccak derives from the intricate, multi-round permutation f that its authors developed.[6] The RC4-redesign called Spritz refers to the sponge-construct to define the algorithm.
For another example, a sponge function can be used to build authenticated encryption with associated data (AEAD).[3]
References
- ^ The Keccak Team. "Duplexing The Sponge" (PDF).
- ^ Guido Bertoni, Joan Daemen, Michaël Peeters and Gilles Van Assche. "Sponge Functions". Ecrypt Hash Workshop 2007.
{{cite web}}: CS1 maint: multiple names: authors list (link) - ^ a b Rivest, Ron; Schuldt, Jacob (2014-10-27). "Spritz - a spongy RC4-like stream cipher and hash function" (PDF). Retrieved 2014-12-29.
- ^ a b Guido Bertoni, Joan Daemen, Michaël Peeters and Gilles Van Assche. "Duplexing the sponge: single-pass authenticated encryption and other applications" (PDF).
{{cite web}}: CS1 maint: multiple names: authors list (link) - ^ Guido Bertoni, Joan Daemen, Michaël Peeters and Gilles Van Assche. "On the Indifferentiability of the Sponge Construction". EuroCrypt 2008.
{{cite web}}: CS1 maint: multiple names: authors list (link) - ^ Boutin, Chad (2 October 2012). "NIST Selects Winner of Secure Hash Algorithm (SHA-3) Competition". NIST. Retrieved 4 October 2012.


