Qubes OS: Difference between revisions
→External links: +link |
|||
| Line 74: | Line 74: | ||
* [http://invisiblethingslab.com/itl/Welcome.html Invisible Things Lab] |
* [http://invisiblethingslab.com/itl/Welcome.html Invisible Things Lab] |
||
* [http://distrowatch.com/table.php?distribution=qubes DistroWatch Overview] |
* [http://distrowatch.com/table.php?distribution=qubes DistroWatch Overview] |
||
* [http://qubes-os.org Qubes OS Homepage] |
|||
{{RedHatFedora-distro}} |
{{RedHatFedora-distro}} |
||
Revision as of 20:18, 28 February 2013
| File:Qubes OS logo.png | |
 Applications running in different security domains | |
| Developer | Invisible Things Lab |
|---|---|
| OS family | Unix-like |
| Working state | Current |
| Source model | Free and open source software (except for Windows Support Tools)[1] |
| Initial release | 2012/09/03[2] |
| Latest release | 1.0 / September 3, 2012 |
| Available in | Multilingual |
| Update method | Yum (PackageKit) |
| Package manager | RPM Package Manager |
| Platforms | x86-64 |
| Kernel type | Hybrid (Xen and Linux) |
| Userland | Fedora |
| Default user interface | KDE |
| License | GPL v2 |
| Official website | qubes-os.org |
Qubes OS is a desktop environment that aims to provide security through isolation[3]. Virtualization is performed by Xen, and user environments are based on Fedora.
Security goals
Qubes implements a Security by Isolation approach.[4] The assumption is that there can be no perfect, bug-free desktop environment. Such an environment counts milions of lines of code, billions of software/hardware interactions. One critical bug in any of these interactions is enough for a malicious software to take control over a machine. [5]
In order to secure our desktop, we should take care of isolating various environments, so that if one of the components get compromised, the malicious software get access to a very limited amount of personal data.
The isolation is provided in two dimensions: hardware controllers are isolated into functional domains (GUI, network and storage domains), whereas the user's digital life is devided in domains with differents levels of trust: for instance work domain (most trusted), shopping domain, random domain (less trusted).[6] Each of those domains is run in a separate virtual machine.
Qubes is not a multi-user system.
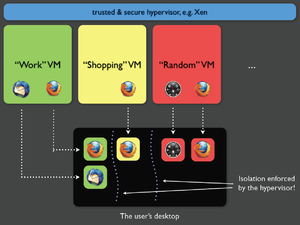
System architecture overview
Xen hypervisor and administrative domain (Dom0)
The hypervisor provides isolation between different virtual machines. The administrative domain, also referred to as Dom0, has direct access to hardware. Dom0 hosts the GUI domain and controlls the graphics device, as well as input devices, such as keyboard and mouse. The GUI domain runs the X server which displays the user desktop, and the Window Manager that allows to start and stop the applications and manipulate their windows.
Integration of the different virtual machines is provided by the Application Viewer, which provides an illusion for the user that applications execute natively on the desktop, while in fact they are hosted (and isolated) in different virtual machines. Qubes integrates all these virtual machines onto one common desktop environment.
Because Dom0 is security-sensitive, it is isolated from the network. It tends to have as little interface and communication whith other domains as possible in order to minimize the possibility of an attack originating from an infected virtual machine.[7] [8]
The network domain
The network mechanism is the most exposed to security attacks. This is why it is isolated in a separate, unprivileged virtual machine, called the Network Domain.
An additional proxy virtual machine is used for advanced networking configuration.[9]
The storage domain
Disk space is saved thanks to the fact that various virtual machines (VM) share the same root file system in a read-only mode. Separate disk storage is only used for userʼs directory and per-VM settings. This allows to centralize software installation and updates. Of course, some softwares can be installed only on a specific VM.
Cryptography is used to protect the filesystems, so that the storage domain cannot read confidential data owned by other domains.
Application Virtual Machines (AppVM)
AppVMs are the virtual machines used for hosting user applications, such as a web browser, an e-mail client or a text editor. For security purpose, these applications can be grouped in different domains, such as “personal”, “work”, “shopping”, “bank”, etc. The security domains are implemented as separate, Virtual Machines (VMs), thus being isolated from each other as if they were executing on different machines.
Some documents or application can be run in disposable VMs through an action available in the file manager. The mechanism follows the idea of sandboxes: after viewing the document or application, then whole Disposable VM get destroyed.[10]
Each security domain is labelled by a color, and each window is marked by the color of the domain it belongs to. Thanks to that approach it is always clearly visible to which domain a given window belongs.

References
- ^ "Qubes OS License".
- ^ "Introducing Qubes 1.0!". 2012/09/03.
{{cite news}}: Check date values in:|date=(help) - ^ "Qubes OS bakes in virty system-level security". The Register. 5 September 2012.
- ^ "The three approaches to computer security". Joanna Rutkowska. September 02, 2008.
{{cite web}}: Check date values in:|date=(help) - ^ "Qubes OS: An Operating System Designed For Security". tom's hardware. August 30, 2011.
- ^ "Partitioning my digital life into security domains". Joanna Rutkowska. March 13, 2011.
- ^ "(Un)Trusting your GUI Subsystem". Joanna Rutkowska. September 09, 2010.
{{cite web}}: Check date values in:|date=(help) - ^ "The Linux Security Circus: On GUI isolation". Joanna Rutkowska. April 23, 2011.
- ^ "Playing with Qubes Networking for Fun and Profit". Joanna Rutkowska. September 28, 2011.
- ^ "Qubes To Implement Disposable Virtual Machines". OSnews. 3rd Jun 2010.
{{cite web}}: Check date values in:|date=(help)
