Internet of things: Difference between revisions
Undid revision 745146014 by 204.136.186.133 (talk) worse grammar |
|||
| Line 24: | Line 24: | ||
}}</ref> Besides using RFID, the ''[[Tag (metadata)|tagging]]'' of things may be achieved through such technologies as [[near field communication]], [[barcodes]], [[QR codes]] and [[digital watermarking]].<ref>Techvibes [http://www.techvibes.com/blog/from-m2m-to-the-internet-of-things-viewpoints-from-europe-2011-07-07 ''From M2M to The Internet of Things: Viewpoints From Europe''] 7 July 2011</ref><ref>Dr. Lara Sristava, European Commission Internet of Things Conference in Budapest, 16 May 2011 [http://www.youtube.com/watch?v=CJdNq7uSddM ''The Internet of Things – Back to the Future (Presentation)'']</ref> |
}}</ref> Besides using RFID, the ''[[Tag (metadata)|tagging]]'' of things may be achieved through such technologies as [[near field communication]], [[barcodes]], [[QR codes]] and [[digital watermarking]].<ref>Techvibes [http://www.techvibes.com/blog/from-m2m-to-the-internet-of-things-viewpoints-from-europe-2011-07-07 ''From M2M to The Internet of Things: Viewpoints From Europe''] 7 July 2011</ref><ref>Dr. Lara Sristava, European Commission Internet of Things Conference in Budapest, 16 May 2011 [http://www.youtube.com/watch?v=CJdNq7uSddM ''The Internet of Things – Back to the Future (Presentation)'']</ref> |
||
In its original interpretation,{{when|date=August 2014}} one of the first consequences of implementing the internet of things by equipping all objects in the world with minuscule identifying devices or machine-readable identifiers would be to transform daily life.<ref>P. Magrassi, A. Panarella, N. Deighton, G. Johnson, ''Computers to Acquire Control of the Physical World'', Gartner research report T-14-0301, 28 September 2001 |
|||
</ref><ref name=casal> |
</ref><ref name=casal> |
||
Casaleggio Associati [http://www.slideshare.net/casaleggioassociati/the-evolution-of-internet-of-things ''The Evolution of Internet of Things''] February 2011 {{Request quote|date=August 2014}} |
Casaleggio Associati [http://www.slideshare.net/casaleggioassociati/the-evolution-of-internet-of-things ''The Evolution of Internet of Things''] February 2011 {{Request quote|date=August 2014}} |
||
</ref> |
</ref> |
||
For instance, |
For instance, instant and ceaseless [[inventory control]] would become ubiquitous.<ref name=casal /> A person's ability to interact with objects could be altered remotely based on immediate or present needs, in accordance with existing [[end-user]] agreements.<ref name="gartner.com"/> For example, such technology could grant motion-picture publishers much more control over end-user private devices by remotely enforcing [[copyright|copyright restrictions]] and [[digital rights management]], so the ability of a customer who bought a [[Blu-ray disc]] to watch the movie becomes dependent on so-called "copyright holder's" decision, similar to Circuit City's failed [[DIVX]]. |
||
==Applications== |
==Applications== |
||
Revision as of 15:17, 19 October 2016

The internet of things (IoT) is the internetworking of physical devices, vehicles (also referred to as "connected devices" and "smart devices"), buildings and other items—embedded with electronics, software, sensors, actuators, and network connectivity that enable these objects to collect and exchange data.[1][2][3] In 2013 the Global Standards Initiative on Internet of Things (IoT-GSI) defined the IoT as "the infrastructure of the information society." [4] The IoT allows objects to be sensed and/or controlled remotely across existing network infrastructure,[5] creating opportunities for more direct integration of the physical world into computer-based systems, and resulting in improved efficiency, accuracy and economic benefit.[6][7][8][9][10][11] When IoT is augmented with sensors and actuators, the technology becomes an instance of the more general class of cyber-physical systems, which also encompasses technologies such as smart grids, smart homes, intelligent transportation and smart cities. Each thing is uniquely identifiable through its embedded computing system but is able to interoperate within the existing Internet infrastructure. Experts estimate that the IoT will consist of almost 50 billion objects by 2020.[12]
British entrepreneur Kevin Ashton coined the term in 1999 while working at Auto-ID Labs (originally called Auto-ID centers, referring to a global network of objects connected to radio-frequency identification, or RFID).[13] Typically, IoT is expected to offer advanced connectivity of devices, systems, and services that goes beyond machine-to-machine (M2M) communications and covers a variety of protocols, domains, and applications.[14] The interconnection of these embedded devices (including smart objects), is expected to usher in automation in nearly all fields, while also enabling advanced applications like a smart grid,[15] and expanding to the areas such as smart cities.[16][17]
"Things," in the IoT sense, can refer to a wide variety of devices such as heart monitoring implants, biochip transponders on farm animals, electric clams in coastal waters,[18] automobiles with built-in sensors, DNA analysis devices for environmental/food/pathogen monitoring[19] or field operation devices that assist firefighters in search and rescue operations.[20] Legal scholars suggest to look at "Things" as an "inextricable mixture of hardware, software, data and service".[21] These devices collect useful data with the help of various existing technologies and then autonomously flow the data between other devices.[22] Current market examples include home automation (also known as smart home devices) such as the control and automation of lighting, heating (like smart thermostat), ventilation, air conditioning (HVAC) systems, and appliances such as washer/dryers, ovens or refrigerators/freezers that use Wi-Fi for remote monitoring.
As well as the expansion of Internet-connected automation into a plethora of new application areas, IoT is also expected to generate large amounts of data from diverse locations, with the consequent necessity for quick aggregation of the data, and an increase in the need to index, store, and process such data more effectively. IoT is one of the platforms of today's Smart City, and Smart Energy Management Systems.[23][24]
History
As of 2016[update], the vision of the internet of things has evolved due to a convergence of multiple technologies, including ubiquitous wireless communication, real-time analytics, machine learning, commodity sensors, and embedded systems.[20] This means that the traditional fields of embedded systems, wireless sensor networks, control systems, automation (including home and building automation), and others all contribute to enabling the internet of things[25] (IoT).
The concept of a network of smart devices was discussed as early as 1982, with a modified Coke machine at Carnegie Mellon University becoming the first internet-connected appliance,[26] able to report its inventory and whether newly loaded drinks were cold.[27] Mark Weiser's seminal 1991 paper on ubiquitous computing, "The Computer of the 21st Century", as well as academic venues such as UbiComp and PerCom produced the contemporary vision of IoT.[28][29] In 1994 Reza Raji described the concept in IEEE Spectrum as "[moving] small packets of data to a large set of nodes, so as to integrate and automate everything from home appliances to entire factories".[30] Between 1993 and 1996 several companies proposed solutions like Microsoft's at Work or Novell's NEST. However, only in 1999 did the field start gathering momentum. Bill Joy envisioned Device to Device (D2D) communication as part of his "Six Webs" framework, presented at the World Economic Forum at Davos in 1999.[31]
The concept of the internet of things first became popular in 1999, through the Auto-ID Center at MIT and related market-analysis publications.[32] Radio-frequency identification (RFID) was seen by Kevin Ashton (one of the founders of the original Auto-ID Center) as a prerequisite for the internet of things at that point.[33] If all objects and people in daily life were equipped with identifiers, computers could manage and inventory them.[34][35] Besides using RFID, the tagging of things may be achieved through such technologies as near field communication, barcodes, QR codes and digital watermarking.[36][37]
In its original interpretation,[when?] one of the first consequences of implementing the internet of things by equipping all objects in the world with minuscule identifying devices or machine-readable identifiers would be to transform daily life.[38][39] For instance, instant and ceaseless inventory control would become ubiquitous.[39] A person's ability to interact with objects could be altered remotely based on immediate or present needs, in accordance with existing end-user agreements.[33] For example, such technology could grant motion-picture publishers much more control over end-user private devices by remotely enforcing copyright restrictions and digital rights management, so the ability of a customer who bought a Blu-ray disc to watch the movie becomes dependent on so-called "copyright holder's" decision, similar to Circuit City's failed DIVX.
Applications


According to Gartner, Inc. (a technology research and advisory corporation), there will be nearly 20.8 billion devices on the internet of things by 2020.[40] ABI Research estimates that more than 30 billion devices will be wirelessly connected to the internet of things by 2020.[41] As per a recent survey and study done by Pew Research Internet Project, a large majority of the technology experts and engaged Internet users who responded—83 percent—agreed with the notion that the Internet/Cloud of Things, embedded and wearable computing (and the corresponding dynamic systems[42]) will have widespread and beneficial effects by 2025.[43] As such, it is clear that the IoT will consist of a very large number of devices being connected to the Internet.[44] In an active move to accommodate new and emerging technological innovation, the UK Government, in their 2015 budget, allocated £40,000,000 towards research into the internet of things. The former British Chancellor of the Exchequer George Osborne, posited that the internet of things is the next stage of the information revolution and referenced the inter-connectivity of everything from urban transport to medical devices to household appliances.[45]
Integration with the Internet implies that devices will use an IP address as a unique identifier. However, due to the limited address space of IPv4 (which allows for 4.3 billion unique addresses), objects in the IoT will have to use IPv6 to accommodate the extremely large address space required.[46][47][48][49][50] Objects in the IoT will not only be devices with sensory capabilities, but also provide actuation capabilities (e.g., bulbs or locks controlled over the Internet).[51] To a large extent, the future of the internet of things will not be possible without the support of IPv6; and consequently the global adoption of IPv6 in the coming years will be critical for the successful development of the IoT in the future.[47][48][49][50]
The ability to network embedded devices with limited CPU, memory and power resources means that IoT finds applications in nearly every field.[52] Such systems could be in charge of collecting information in settings ranging from natural ecosystems to buildings and factories,[51] thereby finding applications in fields of environmental sensing and urban planning.[53]
On the other hand, IoT systems could also be responsible for performing actions, not just sensing things. Intelligent shopping systems, for example, could monitor specific users' purchasing habits in a store by tracking their specific mobile phones. These users could then be provided with special offers on their favorite products, or even location of items that they need, which their fridge has automatically conveyed to the phone.[54][55] Additional examples of sensing and actuating are reflected in applications that deal with heat, electricity and energy management, as well as cruise-assisting transportation systems.[56]
Other applications that the internet of things can provide is enabling extended home security features and home automation.[57] The concept of an "internet of living things" has been proposed to describe networks of biological sensors that could use cloud-based analyses to allow users to study DNA or other molecules.[58] All these advances add to the numerous list of IoT applications. Now with IoT, you can control the electrical devices installed in your house while you are sorting out your files in office. Your water will be warm as soon as you get up in the morning for the shower. All credit goes to smart devices which make up the smart home. Everything connected with the help of Internet.[59]
However, the application of the IoT is not only restricted to these areas. Other specialized use cases of the IoT may also exist. An overview of some of the most prominent application areas is provided here. Based on the application domain, IoT products can be classified broadly into five different categories: smart wearable, smart home, smart city, smart environment, and smart enterprise. The IoT products and solutions in each of these markets have different characteristics.[60]
Media
This section may be too technical for most readers to understand. (March 2016) |
In order to hone the manner in which things, media and big data are interconnected, it is first necessary to provide some context into the mechanism used for media process. It has been suggested by Nick Couldry and Joseph Turow that practitioners in media approach big data as many actionable points of information about millions of individuals. The industry appears to be moving away from the traditional approach of using specific media environments such as newspapers, magazines, or television shows and instead tap into consumers with technologies that reach targeted people at optimal times in optimal locations. The ultimate aim is of course to serve, or convey, a message or content that is (statistically speaking) in line with the consumer's mindset. For example, publishing environments are increasingly tailoring messages (advertisements) and content (articles) to appeal to consumers that have been exclusively gleaned through various data-mining activities.[61]
The media industries process big data in a dual, interconnected manner:
- Targeting of consumers (for advertising by marketers)
- Data-capture
Thus, the internet of things creates an opportunity to measure, collect and analyse an ever-increasing variety of behavioural statistics. Cross-correlation of this data could revolutionise the targeted marketing of products and services.[62] For example, as noted by Danny Meadows-Klue, the combination of analytics for conversion tracking with behavioural targeting has unlocked a new level of precision that enables display advertising to be focused on the devices of people with relevant interests.[63] Big data and the IoT work in conjunction. From a media perspective, data is the key derivative of device interconnectivity, whilst being pivotal in allowing clearer accuracy in targeting. The internet of things therefore transforms the media industry, companies and even governments, opening up a new era of economic growth and competitiveness.[64] The wealth of data generated by this industry (i.e. big data) will allow practitioners in advertising and media to gain an elaborate layer on the present targeting mechanisms used by the industry.
Environmental monitoring
Environmental monitoring applications of the IoT typically use sensors to assist in environmental protection[65] by monitoring air or water quality,[18] atmospheric or soil conditions,[66] and can even include areas like monitoring the movements of wildlife and their habitats.[67] Development of resource constrained devices connected to the Internet also means that other applications like earthquake or tsunami early-warning systems can also be used by emergency services to provide more effective aid. IoT devices in this application typically span a large geographic area and can also be mobile.[51] It has been argued that the standardization IoT brings to wireless sensing will revolutionize this area.[68]
Infrastructure management
Monitoring and controlling operations of urban and rural infrastructures like bridges, railway tracks, on- and offshore- wind-farms is a key application of the IoT.[69] The IoT infrastructure can be used for monitoring any events or changes in structural conditions that can compromise safety and increase risk. It can also be used for scheduling repair and maintenance activities in an efficient manner, by coordinating tasks between different service providers and users of these facilities.[51] IoT devices can also be used to control critical infrastructure like bridges to provide access to ships. Usage of IoT devices for monitoring and operating infrastructure is likely to improve incident management and emergency response coordination, and quality of service, up-times and reduce costs of operation in all infrastructure related areas.[70] Even areas such as waste management can benefit from automation and optimization that could be brought in by the IoT.[71]
Manufacturing
Network control and management of manufacturing equipment, asset and situation management, or manufacturing process control bring the IoT within the realm on industrial applications and smart manufacturing as well.[72] The IoT intelligent systems enable rapid manufacturing of new products, dynamic response to product demands, and real-time optimization of manufacturing production and supply chain networks, by networking machinery, sensors and control systems together.[51]
Digital control systems to automate process controls, operator tools and service information systems to optimize plant safety and security are within the purview of the IoT.[69] But it also extends itself to asset management via predictive maintenance, statistical evaluation, and measurements to maximize reliability.[73] Smart industrial management systems can also be integrated with the Smart Grid, thereby enabling real-time energy optimization. Measurements, automated controls, plant optimization, health and safety management, and other functions are provided by a large number of networked sensors.[51]
National Science Foundation established an Industry/University Cooperative Research Center on intelligent maintenance systems (IMS) in 2001 with a research focus to use IoT-based predictive analytics technologies to monitor connected machines and to predict machine degradation, and further to prevent potential failures.[74] The vision to achieve near-zero breakdown using IoT-based predictive analytics led the future development of e-manufacturing and e-maintenance activities.[75]
The term IIOT (industrial internet of things) is often encountered in the manufacturing industries, referring to the industrial subset of the IoT. IIoT in manufacturing would probably generate so much business value that it will eventually lead to the fourth industrial revolution, so the so-called Industry 4.0. It is estimated that in the future, successful companies will be able to increase their revenue through internet of things by creating new business models and improve productivity, exploit analytics for innovation, and transform workforce.[76] The potential of growth by implementing IIoT will generate $12 trillion of global GDP by 2030.[76]
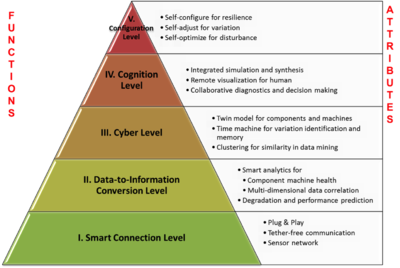
While connectivity and data acquisition are imperative for IIoT, they should be the foundation and path to something bigger but not the purpose. Among all the technologies, predictive maintenance is probably a relatively "easier win" since it is applicable to existing assets and management systems. The objective of intelligent maintenance systems is to reduce unexpected downtime and increase productivity. And to realize that alone would generate around up to 30% over total maintenance costs.[76] Industrial big data analytics will play a vital role in manufacturing asset predictive maintenance, although that is not the only capability of industrial big data.[78][79] Cyber-physical systems (CPS) is the core technology of industrial big data and it is will be an interface between human and the cyber world. Cyber-physical systems can be designed by following the 5C (connection, conversion, cyber, cognition, configuration) architecture,[77] and it will transform the collected data into actionable information, and eventually interfere with the physical assets to optimize processes.
An IoT-enabled intelligent system of such cases has been demonstrated by the NSF Industry/University Collaborative Research Center for Intelligent Maintenance Systems (IMS) at University of Cincinnati on a band saw machine in IMTS 2014 in Chicago.[80] Band saw machines are not necessarily expensive, but the band saw belt expenses are enormous since they degrade much faster. However, without sensing and intelligent analytics, it can be only determined by experience when the band saw belt will actually break. The developed prognostics system will be able to recognize and monitor the degradation of band saw belts even if the condition is changing, so that users will know in near real time when is the best time to replace band saw. This will significantly improve user experience and operator safety, and save costs on replacing band saw belts before they actually break. The developed analytical algorithms were realized on a cloud server, and was made accessible via the Internet and on mobile devices.[80]
Energy management
Integration of sensing and actuation systems, connected to the Internet, is likely to optimize energy consumption as a whole.[51] It is expected that IoT devices will be integrated into all forms of energy consuming devices (switches, power outlets, bulbs, televisions, etc.) and be able to communicate with the utility supply company in order to effectively balance power generation and energy usage.[81] Such devices would also offer the opportunity for users to remotely control their devices, or centrally manage them via a cloud based interface, and enable advanced functions like scheduling (e.g., remotely powering on or off heating systems, controlling ovens, changing lighting conditions etc.).[51]
Besides home based energy management, the IoT is especially relevant to the Smart Grid since it provides systems to gather and act on energy and power-related information in an automated fashion with the goal to improve the efficiency, reliability, economics, and sustainability of the production and distribution of electricity.[81] Using advanced metering infrastructure (AMI) devices connected to the Internet backbone, electric utilities can not only collect data from end-user connections, but also manage other distribution automation devices like transformers and reclosers.[51]
Medical and healthcare
IoT devices can be used to enable remote health monitoring and emergency notification systems. These health monitoring devices can range from blood pressure and heart rate monitors to advanced devices capable of monitoring specialized implants, such as pacemakers, Fitbit electronic wristbands or advanced hearing aids.[51] Specialized sensors can also be equipped within living spaces to monitor the health and general well-being of senior citizens, while also ensuring that proper treatment is being administered and assisting people regain lost mobility via therapy as well.[82] Other consumer devices to encourage healthy living, such as, connected scales or wearable heart monitors, are also a possibility with the IoT.[83] More and more end-to-end health monitoring IoT platforms are coming up for antenatal and chronic patients, helping one manage health vitals and recurring medication requirements.[citation needed]
Building and home automation
IoT devices can be used to monitor and control the mechanical, electrical and electronic systems used in various types of buildings (e.g., public and private, industrial, institutions, or residential)[51] in home automation and building automation systems.
Transportation

The IoT can assist in integration of communications, control, and information processing across various transportation systems. Application of the IoT extends to all aspects of transportation systems (i.e. the vehicle, the infrastructure, and the driver or user). Dynamic interaction between these components of a transport system enables inter and intra vehicular communication, smart traffic control, smart parking, electronic toll collection systems, logistic and fleet management, vehicle control, and safety and road assistance.[51]
Metropolitan scale deployments
There are several planned or ongoing large-scale deployments of the IoT, to enable better management of cities and systems. For example, Songdo, South Korea, the first of its kind fully equipped and wired smart city, is near completion. Nearly everything in this city is planned to be wired, connected and turned into a constant stream of data that would be monitored and analyzed by an array of computers with little, or no human intervention. [citation needed]
Another application is a currently undergoing project in Santander, Spain. For this deployment, two approaches have been adopted. This city of 180,000 inhabitants, has already seen 18,000 city application downloads for their smartphones. This application is connected to 10,000 sensors that enable services like parking search, environmental monitoring, digital city agenda among others. City context information is used in this deployment so as to benefit merchants through a spark deals mechanism based on city behavior that aims at maximizing the impact of each notification.[84]
Other examples of large-scale deployments underway include the Sino-Singapore Guangzhou Knowledge City;[85] work on improving air and water quality, reducing noise pollution, and increasing transportation efficiency in San Jose, California;[86] and smart traffic management in western Singapore.[87] French company, Sigfox, commenced building an ultra-narrowband wireless data network in the San Francisco Bay Area in 2014, the first business to achieve such a deployment in the U.S.[88][89] It subsequently announced it would set up a total of 4000 base stations to cover a total of 30 cities in the U.S. by the end of the 2016, making it the largest IoT network coverage provider in the country thus far.[90][91]
Another example of a large deployment is the one completed by New York Waterways in New York City to connect all their vessels and being able to monitor them live 24/7. The network was designed and engineered by Fluidmesh Networks, a Chicago-based company developing wireless networks for critical applications. The NYWW network is currently providing coverage on the Hudson River, East River, and Upper New York Bay. With the wireless network in place, NY Waterway is able to take control of its fleet and passengers in a way that was not previously possible. New applications can include security, energy and fleet management, digital signage, public Wi-Fi, paperless ticketing and others.[92]
Consumer application
A growing portion of IoT devices are created for consumer use. Examples of consumer applications include connected car, entertainment, residences and smart homes, wearable technology, quantified self, connected health, and smart retail. Consumer IoT provides new opportunities for user experience and interfaces.
Some consumer applications have been criticized for their lack of redundancy and their inconsistency, leading to a popular parody known as the “Internet of Shit.”[93] Companies have been criticized for their rush into IoT, creating devices of questionable value,[94] and not setting up stringent security standards.[95]
Unique addressability of things
The original idea of the Auto-ID Center is based on RFID-tags and unique identification through the Electronic Product Code however this has evolved into objects having an IP address or URI.
An alternative view, from the world of the Semantic Web[96] focuses instead on making all things (not just those electronic, smart, or RFID-enabled) addressable by the existing naming protocols, such as URI. The objects themselves do not converse, but they may now be referred to by other agents, such as powerful centralized servers acting for their human owners.
The next generation of Internet applications using Internet Protocol version 6 (IPv6) would be able to communicate with devices attached to virtually all human-made objects because of the extremely large address space of the IPv6 protocol. This system would therefore be able to scale to the large numbers of objects envisaged.[97]
A combination of these ideas can be found in the current GS1/EPCglobal EPC Information Services[98] (EPCIS) specifications. This system is being used to identify objects in industries ranging from aerospace to fast moving consumer products and transportation logistics.[99]
Trends and characteristics

Intelligence
Ambient intelligence and autonomous control are not part of the original concept of the internet of things. Ambient intelligence and autonomous control do not necessarily require Internet structures, either. However, there is a shift in research to integrate the concepts of the internet of things and autonomous control, with initial outcomes towards this direction considering objects as the driving force for autonomous IoT.
In the future the internet of things may be a non-deterministic and open network in which auto-organized or intelligent entities (Web services, SOA components), virtual objects (avatars) will be interoperable and able to act independently (pursuing their own objectives or shared ones) depending on the context, circumstances or environments. Autonomous behavior through the collection and reasoning of context information as well as the objects ability to detect changes in the environment, faults affecting sensors and introduce suitable mitigation measures constitute a major research trend,[100] clearly needed to provide credibility to the IoT technology. Modern IoT products and solutions in the marketplace use a variety of different technologies to support such context-aware automation but more sophisticated forms of intelligence are requested to permit sensor units to be deployed in real environments.
Architecture
The system will likely be an example of event-driven architecture,[101] bottom-up made (based on the context of processes and operations, in real-time) and will consider any subsidiary level. Therefore, model driven and functional approaches will coexist with new ones able to treat exceptions and unusual evolution of processes (multi-agent systems, B-ADSc, etc.).
In an internet of things, the meaning of an event will not necessarily be based on a deterministic or syntactic model but would instead be based on the context of the event itself: this will also be a semantic web.[102] Consequently, it will not necessarily need common standards that would not be able to address every context or use: some actors (services, components, avatars) will accordingly be self-referenced and, if ever needed, adaptive to existing common standards (predicting everything would be no more than defining a "global finality" for everything that is just not possible with any of the current top-down approaches and standardizations). Some researchers argue that sensor networks are the most essential components of the internet of things.[103]
Building on top of the internet of things, the web of things is an architecture for the application layer of the internet of things looking at the convergence of data from IoT devices into Web applications to create innovative use-cases. In order to program and control the flow of information in the internet of things, a predicted architectural direction is being called BPM Everywhere which is a blending of traditional process management with process mining and special capabilities to automate the control of large numbers of coordinated devices.
Network architecture
The internet of things requires huge scalability in the network space to handle the surge of devices. IETF 6LoWPAN would be used to connect devices to IP networks.With billions of devices[40] being added to the internet space, IPv6 will play a major role in handling the network layer scalability. IETF's Constrained Application Protocol, MQTT and ZeroMQ would provide lightweight data transport.
Fog computing is a viable alternative to prevent such large burst of data flow through Internet. The edge devices' computation power can be used to analyse and process data, thus providing easy real time scalability.
Complexity
In semi-open or closed loops (i.e. value chains, whenever a global finality can be settled) IoT will often be considered and studied as a complex system[105] due to the huge number of different links, interactions between autonomous actors, and its capacity to integrate new actors. At the overall stage (full open loop) it will likely be seen as a chaotic environment (since systems have always finality). As a practical approach, not all elements in the internet of things run in a global, public space. Subsystems are often implemented to mitigate the risks of privacy, control and reliability. For example, Domestic Robotics (Domotics) running inside a smart home might only share data within and be available via a local network.
Size considerations
The Internet of objects would encode 50 to 100 trillion objects, and be able to follow the movement of those objects. Human beings in surveyed urban environments are each surrounded by 1000 to 5000 trackable objects.[106]
Space considerations
In an internet of things, the precise geographic location of a thing—and also the precise geographic dimensions of a thing—will be critical.[107] Therefore, facts about a thing, such as its location in time and space, have been less critical to track because the person processing the information can decide whether or not that information was important to the action being taken, and if so, add the missing information (or decide to not take the action). (Note that some things in the internet of things will be sensors, and sensor location is usually important).[108] The GeoWeb and Digital Earth are promising applications that become possible when things can become organized and connected by location. However, challenges that remain include the constraints of variable spatial scales, the need to handle massive amounts of data, and an indexing for fast search and neighbor operations. If in the internet of things, things are able to take actions on their own initiative, this human-centric mediation role is eliminated, and the time-space context that we as humans take for granted must be given a central role in this information ecosystem. Just as standards play a key role in the Internet and the Web, geospatial standards will play a key role in the internet of things.[citation needed]
Sectors
There are three core sectors of the IoT: enterprise, home, and government, with the enterprise internet of things (EIoT) being the largest of the three. By 2019, the EIoT sector is estimated to account for nearly 40% or 9.1 billion devices.[109]
A "basket of remotes"
According to the CEO of Cisco, the commercial opportunity for "connected products ranging from cars to household goods" is expected to be a $USD 19 trillion.[110] Many IoT devices have a potential to take a piece of this market. Jean-Louis Gassée (Apple initial alumni team, and BeOS co-founder) has addressed this topic in an article on Monday Note,[111] where he predicts that the most likely problem will be what he calls the "basket of remotes" problem, where we'll have hundreds of applications to interface with hundreds of devices that don't share protocols for speaking with one another.
There are multiple approaches to solve this problem, one of them called the "predictive interaction",[112] where cloud or fog based decision makers [clarification needed] will predict the user's next action and trigger some reaction.
For user interaction, new technology leaders are joining forces to create standards for communication between devices. While AllJoyn alliance is composed the top 20 World technology leaders, there are also big companies that promote their own protocol like CCF from Intel.
Manufacturers are becoming more conscious of this problem, and many companies have begun releasing their devices with open APIs. Many of these APIs are used by smaller companies looking to take advantage of quick integration.[citation needed]
Frameworks
Internet-of-things frameworks might help support the interaction between "things" and allow for more-complex structures like distributed computing and the development of distributed applications. Currently, some internet-of-things frameworks seem to focus on real time data logging solutions like Jasper Technologies, Inc. and Xively (formerly Cosm and before that Pachube): offering some basis to work with many "things" and have them interact. Future developments might lead to specific software-development environments to create the software to work with the hardware used in the internet of things. Companies are developing technology platforms to provide this type of functionality for the internet of things. Newer platforms are being developed, which add more intelligence. Foremost, IBM has announced cognitive IoT, which combines traditional IoT with machine intelligence and learning, contextual information, industry-specific models and even natural language processing. The XMPP Standards Foundation (XSF) is creating such a framework in a fully open standard that isn't tied to any company and not connected to any cloud services. This XMPP initiative is called Chatty Things.[113] XMPP provides a set of needed building blocks and a proven distributed solution that can scale with high security levels.
REST is a scalable architecture which allows for things to communicate over Hypertext Transfer Protocol and is easily adopted for IoT applications to provide communication from a thing to a central web server. MQTT is a publish-subscribe architecture on top of TCP/IP which allows for bi-directional communication between a thing and a MQTT broker.
Standards and standards organizations
This section needs expansion. You can help by adding to it. (September 2016) |
This is a list of technical standards for the IoT, most of which are open standards, and the standards organizations that aspire to successfully setting them.
| Short name | Long name | Standards under development | Other notes |
|---|---|---|---|
| Auto-ID Labs | — | Networked RFID (radiofrequency identification) and emerging sensing technologies | |
| EPCglobal | — | Standards for adoption of EPC (Electronic Product Code) technology | |
| FDA | U.S. Food and Drug Administration | UDI (Unique Device Identification) system for unique identifiers for medical devices | |
| GS1 | — | Standards for UIDs (unique identifiers) and RFID of fast-moving consumer goods (consumer packaged goods), health care supplies, and other things | Parent organization comprises member organizations such as GS1 US |
| IETF | Internet Engineering Task Force | Standards that comprise TCP/IP (the Internet protocol suite) | |
| MTConnect Institute | — | MTConnect is a manufacturing industry standard for data exchange with machine tools and related industrial equipment. It is important to the IIoT subset of the IoT. | |
| OCF | Open Connectivity Foundation | Standards for simple devices using CoAP (Constrained Application Protocol) | OCF (Open Connectivity Foundation) supersedes OIC (Open Interconnect Consortium) |
| XSF | XMPP Standards Foundation | Protocol extensions of XMPP (Extensible Messaging and Presence Protocol), the open standard of instant messaging |
Enabling technologies for the IOT
There are many technologies that enable IOT. A key foundation piece is the network used to communicate between nodes of an IOT installation, a role that several wireless and/or wired technologies may fulfill:[114][115][116][117]
- RFID and near-field communication – In the 2000s, RFID was the dominant technology. Later, NFC became dominant (NFC). NFC have become common in smartphones during the early 2010s, with uses such as reading NFC tags or for access to public transportation.[citation needed]
- Rapid developments in the Optical technologies like Li-Fi, Cisco's 40 Gbit/s bidirectional optical technology (BiDi[118]) may aid the development of IoT.
- Optical tags and quick response codes – This is used for low cost tagging. Phone cameras decode QR code using image-processing techniques. In reality QR advertisement campaigns gives less turnout as users need to have another application to read QR codes.
- Bluetooth low energy – This is one of the latest tech. All newly releasing smartphones have BLE hardware in them. Tags based on BLE can signal their presence at a power budget that enables them to operate for up to one year on a lithium coin cell battery.
- Low energy wireless IP networks – embedded radio in system-on-a-chip designs, lower power WiFi, sub-GHz radio in an ISM band, often using a compressed version of IPv6 called 6LowPAN and relying on dedicated routing protocols such as LOADng[119] standardized by the ITU under the recommendation ITU-T G.9903 and RPL.[120]
- ZigBee – This communication technology is based on the IEEE 802.15.4 2.4 GHz-band radio protocol to implement physical and MAC layer for low-rate wireless Private Area Networks. Some of its main characteristics like low power consumption, low data rate, low cost, and high message throughput make it an interesting IoT enabler technology.
- Z-Wave – is a communication protocol that is mostly used in smart home applications. It uses a radio protocol in the 900 MHz-band.
- Thread – Like ZigBee, this IoT communication technology relies on the IEEE 802.15.4 2.4 GHz-band radio protocol. A key difference is that its networking protocol is IPv6-compatible.
- LTE-Advanced – LTE-A is a high-speed communication specification for mobile networks. Compared to its original LTE, LTE-A has been improved to have extended coverage, higher throughput and lower latency. One important application of this technology is Vehicle-to-Vehicle (V2V) communications.
- WiFi-Direct – It is essentially WiFi for peer-to-peer communication without needing to have an access point. This feature attracts IoT applications to be built on top of WiFi-Direct to get benefit from the speed of WiFi while they experience lower latency.
- HaLow - long range, low-power WiFi. Isn't able to transfer much data (bandwidth), yet sufficient for simple devices that require a network connection
- HomePlug – This networking standard can be used to enable IOT communication over a home or building's power lines
- MoCA – This networking standard can be used to enable IOT communication over CATV-type coaxial cable
- Ethernet – This general purpose networking standard can be used to enable IOT communication over twisted pair or fiber network links
Simulation
IOT modeling and simulation (and emulation) is typically carried out at the design stage before deployment of the network. Network simulators like OPNET, NetSim and NS2 can be used to simulate IOT networks.
Politics and civic engagement
Some scholars and activists argue that the IoT can be used to create new models of civic engagement if device networks can be open to user control and inter-operable platforms. Philip N. Howard, a professor and author, writes that political life in both democracies and authoritarian regimes will be shaped by the way the IoT will be used for civic engagement. For that to happen, he argues that any connected device should be able to divulge a list of the "ultimate beneficiaries" of its sensor data, and that individual citizens should be able to add new organizations to the beneficiary list. In addition, he argues that civil society groups need to start developing their IoT strategy for making use of data and engaging with the public.[121]
Government Regulation on IoT
One of the key drivers of the IoT is data. The success of the idea of connecting devices to make them more efficient is dependent upon access to and storage & processing of data. For this purpose companies working on IoT, collect data from multiple sources and store it in their cloud network for further processing. This leaves the door wide open for privacy and security dangers and single point vulnerability of multiple systems.[122] The other issues pertain to consumer choice and ownership of data[123] & how it is used. Presently the regulators have shown more interest in protecting the first three issues identified above.
Current Regulatory Environment:
A report published by the Federal Trade Commission (FTC) in January 2015 made the following three recommendations:[124]
- Data Security – At the time of designing IoT companies should ensure that data collection, storage and processing would be secure at all times. Companies should adopt a “defence in depth” approach and encrypt data at each stage.[125]
- Data consent – users should have a choice as to what data they share with IoT companies and the users must be informed if their data gets exposed.
- Data minimization – IoT companies should collect only the data they need and retain the collected information only for a limited time.
However, the FTC stopped at just making recommendations for now. According to an FTC analysis, the existing framework, consisting of the FTC Act, the Fair Credit Reporting Act, and the Children’s Online Privacy Protection Act, along with developing consumer education and business guidance, participation in multi-stakeholder efforts and advocacy to other agencies at the federal, state and local level, is sufficient to protect consumer rights.[126]
To provide an impetus to the IoT ecosystem, in March 2016, a bipartisan group of four Senators proposed a bill, The Developing Innovation and Growing the Internet of Things (DIGIT) Act, to direct the Federal Communications Commission to assess the need for more spectrum to connect IoT devices. Furthermore, in March 2015, a resolution passed by the Senate recognized the need for formulating a National Policy on IoT and the matter of privacy, security and spectrum is already being considered by the Congress.[127]
Several standards for the IoT industry are actually being established relating to automobiles because most concerns arising from use of connected cars apply to healthcare devices as well. In fact, the National Highway Traffic Safety Administration (NHTSA) is preparing cybersecurity guidelines and a database of best practices to make automotive computer systems more secure.[128]
Criticism and controversies
Platform fragmentation
IoT suffers from platform fragmentation and lack of technical standards[129][130][131][132][133][134][135] a situation where the variety of IoT devices, in terms of both hardware variations and differences in the software running on them, makes the task of developing applications that work consistently between different inconsistent technology ecosystems hard.[136] Customers may be hesitant to bet their IoT future on a proprietary software or hardware devices that uses proprietary protocols that may fade or become difficult to customize and interconnect.[137]
IoT's amorphous computing nature is also a problem for security, since patches to bugs found in the core operating system often do not reach users of older and lower-price devices.[138][139][140] One set of researchers say that the failure of vendors to support older devices with patches and updates leaves more than 87% of active devices vulnerable.[141][142]
Privacy, autonomy and control
Philip N. Howard, a professor and author, writes that the internet of things offers immense potential for empowering citizens, making government transparent, and broadening information access. Howard cautions, however, that privacy threats are enormous, as is the potential for social control and political manipulation.[143]
Concerns about privacy have led many to consider the possibility that Big Data infrastructures such as the IoT and Data Mining are inherently incompatible with privacy.[144] Writer Adam Greenfield claims that these technologies are not only an invasion of public space but are also being used to perpetuate normative behavior, citing an instance of billboards with hidden cameras that tracked the demographics of passersby who stopped to read the advertisement.[145]
The Council of the Internet of Things compared the increased prevalence of digital surveillance due to the Internet of Things to the conceptual panopticon described by Jeremy Bentham in the 18th Century.[146] The assertion was defended by the works of French philosophers Michel Foucault and Gilles Deleuze. Foucault wrote in his novel Discipline and Punish: The Birth of the Prison that the panopticon was a central element of the discipline society developed during the Industrial Era.[147] Foucault also argued that the discipline systems established in factories and school reflected Bentham's vision of panopticism.[147] In his 1992 paper "Postscripts on the Societies of Control," Delueze wrote that the discipline society had transitioned into a control society, with the computer replacing the panopticon as an instrument of discipline and control while still maintaining the qualities similar to that of panopticism.[148]
The privacy of households could be compromised by solely analyzing smart home network traffic patterns without dissecting the contents of encrypted application data, yet a synthetic packet injection scheme can be used to safely overcome such invasion of privacy.[149]
Peter-Paul Verbeek, a professor of philosophy of technology at the University of Twente, Netherlands, writes that technology already influences our moral decision making, which in turn affects human agency, privacy and autonomy. He cautions against viewing technology merely as a human tool and advocates instead to consider it as an active agent.[150]
Justin Brookman, of the Center for Democracy and Technology, expressed concern regarding the impact of IoT on consumer privacy, saying that "There are some people in the commercial space who say, 'Oh, big data — well, let's collect everything, keep it around forever, we'll pay for somebody to think about security later.' The question is whether we want to have some sort of policy framework in place to limit that."[151]
Tim O'Reilly believes that the way companies sell the IoT devices on consumers are misplaced, disputing the notion that the IoT is about gaining efficiency from putting all kinds of devices online and postulating that "IoT is really about human augmentation. The applications are profoundly different when you have sensors and data driving the decision-making."[152]
Editorials at WIRED have also expressed concern, one stating "What you're about to lose is your privacy. Actually, it's worse than that. You aren't just going to lose your privacy, you're going to have to watch the very concept of privacy be rewritten under your nose."[153]
The American Civil Liberties Union (ACLU) expressed concern regarding the ability of IoT to erode people's control over their own lives. The ACLU wrote that "There's simply no way to forecast how these immense powers – disproportionately accumulating in the hands of corporations seeking financial advantage and governments craving ever more control – will be used. Chances are Big Data and the Internet of Things will make it harder for us to control our own lives, as we grow increasingly transparent to powerful corporations and government institutions that are becoming more opaque to us."[154]
Researchers have identified privacy challenges faced by all stakeholders in IoT domain, from the manufacturers and app developers to the consumers themselves, and examined the responsibility of each party in order to ensure user privacy at all times. Problems highlighted by the report[155] include:
- User consent – somehow, the report says, users need to be able to give informed consent to data collection. Users, however, have limited time and technical knowledge.
- Freedom of choice – both privacy protections and underlying standards should promote freedom of choice.
- Anonymity – IoT platforms pay scant attention to user anonymity when transmitting data, the researchers note. Future platforms could, for example, use TOR or similar technologies so that users can't be too deeply profiled based on the behaviors of their "things".
In response to rising concerns about privacy and smart technology, in 2007 the British Government stated it would follow formal Privacy by Design principles when implementing their smart metering program. The program would lead to replacement of traditional power meters with smart power meters, which could track and manage energy usage more accurately.[156] However the British Computer Society is doubtful these principles were ever actually implemented.[157] In 2009 the Dutch Parliament rejected a similar smart metering program, basing their decision on privacy concerns. The Dutch program later revised and passed in 2011.[157]
Security
Concerns have been raised that the internet of things is being developed rapidly without appropriate consideration of the profound security challenges involved[158] and the regulatory changes that might be necessary.[159] According to the Business Insider Intelligence Survey conducted in the last quarter of 2014, 39% of the respondents said that security is the biggest concern in adopting internet-of-things technology.[160] In particular, as the internet of things spreads widely, cyber attacks are likely to become an increasingly physical (rather than simply virtual) threat.[161] In a January 2014 article in Forbes, cybersecurity columnist Joseph Steinberg listed many Internet-connected appliances that can already "spy on people in their own homes" including televisions, kitchen appliances,[162] cameras, and thermostats.[163] Computer-controlled devices in automobiles such as brakes, engine, locks, hood and truck releases, horn, heat, and dashboard have been shown to be vulnerable to attackers who have access to the onboard network. In some cases, vehicle computer systems are internet-connected, allowing them to be exploited remotely.[164] By 2008 security researchers had shown the ability to remotely control pacemakers without authority. Later hackers demonstrated remote control of insulin pumps [165] and implantable cardioverter defibrillators.[166] David Pogue wrote[167] that some recently published reports about hackers remotely controlling certain functions of automobiles were not as serious as one might otherwise guess because of various mitigating circumstances; such as the bug that allowed the hack having been fixed before the report was published, or that the hack required security researchers having physical access to the car prior to the hack to prepare for it.
The U.S. National Intelligence Council in an unclassified report maintains that it would be hard to deny "access to networks of sensors and remotely-controlled objects by enemies of the United States, criminals, and mischief makers... An open market for aggregated sensor data could serve the interests of commerce and security no less than it helps criminals and spies identify vulnerable targets. Thus, massively parallel sensor fusion may undermine social cohesion, if it proves to be fundamentally incompatible with Fourth-Amendment guarantees against unreasonable search."[168] In general, the intelligence community views internet of things as a rich source of data.[169]
As a response to increasing concerns over security, the Internet of Things Security Foundation (IoTSF) was launched on 23 September 2015. IoTSF has a mission to secure the internet of things by promoting knowledge and best practice. Its founding board is made from technology providers and telecommunications companies including BT, Vodafone, Imagination Technologies and Pen Test Partners.[170][171]
Design
Given widespread recognition of the evolving nature of the design and management of the internet of things, sustainable and secure deployment of internet-of-things solutions must design for "anarchic scalability."[172] Application of the concept of anarchic scalability can be extended to physical systems (i.e. controlled real-world objects), by virtue of those systems being designed to account for uncertain management futures. This "hard anarchic scalability" thus provides a pathway forward to fully realize the potential of internet-of-things solutions by selectively constraining physical systems to allow for all management regimes without risking physical failure.
Brown University computer scientist Michael Littman has argued that successful execution of the internet of things requires consideration of the interface's usability as well as the technology itself. These interfaces need to be not only more user-friendly but also better integrated: "If users need to learn different interfaces for their vacuums, their locks, their sprinklers, their lights, and their coffeemakers, it's tough to say that their lives have been made any easier."[173]
Environmental sustainability impact
A concern regarding IoT technologies pertains to the environmental impacts of the manufacture, use, and eventual disposal of all these semiconductor-rich devices.[174] Modern electronics are replete with a wide variety of heavy metals and rare-earth metals, as well as highly toxic synthetic chemicals. This makes them extremely difficult to properly recycle. Electronic components are often incinerated or placed in regular landfills. Furthermore, the human and environmental cost of mining the rare-earth metals that are integral to modern electronic components continues to grow. With production of electronic equipment growing globally yet little of the metals (from end-of-life equipment) being recovered for reuse, the environmental impacts can be expected to increase.
Also, because the concept of IoT entails adding electronics to mundane devices (for example, simple light switches), and because the major driver for replacement of electronic components is often technological obsolescence rather than actual failure to function, it is reasonable to expect that items that previously were kept in service for many decades would see an accelerated replacement cycle, if they were part of the IoT. For example, a traditional house built with 30 light switches and 30 electrical outlets might stand for 50 years, with all those components still original at the end of that period. But a modern house built with the same number of switches and outlets set up for IoT might see each switch and outlet replaced at five-year intervals, in order to keep up-to-date with technological changes. This translates into a ten-fold increase in waste requiring disposal.
Intentional obsolescence of devices
The Electronic Frontier Foundation has raised concerns that companies can use the technologies necessary to support connected devices to intentionally disable or "brick" their customers' devices via a remote software update or by disabling a service necessary to the operation of the device. In one example, home automation devices sold with the promise of a "Lifetime Subscription" were rendered useless after Nest Labs acquired Revolv and made the decision to shut down the central servers the Revolv devices had used to operate.[175] As Nest is a company owned by Alphabet (Google's parent company), the EFF argues this sets a "terrible precedent for a company with ambitions to sell self-driving cars, medical devices, and other high-end gadgets that may be essential to a person's livelihood or physical safety."[176]
Owners should be free to point their devices to a different server or collaborate on improved software. But such action violates the United States DMCA section 1201, that only has an exemption for "local use". This forces tinkerers that want to keep using their own equipment into a legal grey area. EFF thinks buyers should refuse electronics and software that prioritize the manufacturer's wishes above their own.[176]
Examples of post sale manipulations include Google Nest Revolv, disabled privacy settings on Android, Sony disabling GNU/Linux on PlayStation 3, enforced EULA on Wii U.[176]
Trivia
Kevin Ashton, the originator of the term "Internet of Things", revealed to the BBC that he now wishes he had phrased IoT as the "Internet for Things".[177]
See also
References
- ^ http://www.linux.com/news/who-needs-internet-things Who Needs the Internet of Things? (Linux.com)
- ^ http://www.linux.com/NEWS/21-OPEN-SOURCE-PROJECTS-IOT 21 Open Source Projects for IoT (Linux.com)
- ^ "Internet of Things Global Standards Initiative". ITU. Retrieved 26 June 2015.
- ^ "Internet of Things Global Standards Initiative". ITU. Retrieved 1 June 2016.
- ^ https://hbr.org/resources/pdfs/comm/verizon/18980_HBR_Verizon_IoT_Nov_14.pdf
- ^ http://www.internet-of-things-research.eu/pdf/Converging_Technologies_for_Smart_Environments_and_Integrated_Ecosystems_IERC_Book_Open_Access_2013.pdf
- ^ http://www.cisco.com/web/solutions/trends/iot/introduction_to_IoT_november.pdf
- ^ http://cordis.europa.eu/fp7/ict/enet/documents/publications/iot-between-the-internet-revolution.pdf
- ^ http://www.vs.inf.ethz.ch/publ/papers/Internet-of-things.pdf
- ^ http://www.cognizant.com/InsightsWhitepapers/Reaping-the-Benefits-of-the-Internet-of-Things.pdf
- ^ "The Supply Chain: Changing at the Speed of Technology". Retrieved 18 September 2015.
- ^ Dave Evans (April 2011). "The Internet of Things: How the Next Evolution of the Internet Is Changing Everything" (PDF). Cisco. Retrieved 15 February 2016.
- ^ Wood, Alex. "The internet of things is revolutionizing our lives, but standards are a must". theguardian.com. The Guardian. Retrieved 31 March 2015.
- ^ J. Höller, V. Tsiatsis, C. Mulligan, S. Karnouskos, S. Avesand, D. Boyle: From Machine-to-Machine to the Internet of Things: Introduction to a New Age of Intelligence. Elsevier, 2014, ISBN 978-0-12-407684-6.
- ^ O. Monnier: A smarter grid with the Internet of Things. Texas Instruments, 2013.
- ^ https://www.itu.int/dms_pub/itu-t/oth/0b/15/T0B150000153301PDFE.pdf
- ^ "IEEE Xplore Full-Text PDF:". Retrieved 26 June 2015.
- ^ a b "Molluscan eye". Retrieved 26 June 2015.
- ^ Erlich, Yaniv (2015). "A vision for ubiquitous sequencing". Genome Research. 25 (10): 1411–1416. doi:10.1101/gr.191692.115. ISSN 1088-9051. PMC 4579324. PMID 26430149.
- ^ a b I. Wigmore: "Internet of Things (IoT)". TechTarget, June 2014.
- ^ Noto La Diega, Guido and Walden, Ian, Contracting for the 'Internet of Things': Looking into the Nest (February 1, 2016). Queen Mary School of Law Legal Studies Research Paper No. 219/2016. Available at SSRN: http://ssrn.com/abstract=2725913
- ^ Hendricks, Drew. "The Trouble with the Internet of Things". London Datastore. Greater London Authority. Retrieved 10 August 2015.
- ^ Violino, Bob. "The 'Internet of things' will mean really, really big data". InfoWorld. Retrieved 9 July 2014.
- ^ Hogan, Michael. "The 'The Internet of Things Database' Data Management Requirements". ScaleDB. Retrieved 15 July 2014.
- ^ "Internet of Things (IoT)".
- ^ "The "Only" Coke Machine on the Internet". Carnegie Mellon University. Retrieved 10 November 2014.
- ^ "Internet of Things Done Wrong Stifles Innovation". InformationWeek. 7 July 2014. Retrieved 10 November 2014.
- ^ Mattern, Friedemann; Christian Floerkemeier (2010). "From the Internet of Computers to the Internet of Things" (PDF). Informatik- Spektrum. 33 (2): 107–121. doi:10.1007/s00287-010-0417-7. Retrieved 3 February 2014.
- ^ Weiser, Mark (1991). "The Computer for the 21st Century" (PDF). Scientific American. 265 (3): 94–104. Bibcode:1991SciAm.265c..94W. doi:10.1038/scientificamerican0991-94. Retrieved 5 November 2014.
- ^ Raji, RS (June 1994). "Smart networks for control". IEEE Spectrum.
- ^ Jason Pontin: ETC: Bill Joy's Six Webs. In: MIT Technology Review, 29 September 2005. Retrieved 17 November 2013.
- ^ Analyst Anish Gaddam interviewed by Sue Bushell in Computerworld, on 24 July 2000 ("M-commerce key to ubiquitous internet")
- ^ a b P. Magrassi, Why a Universal RFID Infrastructure Would Be a Good Thing, Gartner research report G00106518, 2 May 2002 [1]
- ^ P. Magrassi, T. Berg, A World of Smart Objects, Gartner research report R-17-2243, 12 August 2002 [2]
- ^ Commission of the European Communities (18 June 2009). "Internet of Things — An action plan for Europe" (PDF). COM(2009) 278 final.
- ^ Techvibes From M2M to The Internet of Things: Viewpoints From Europe 7 July 2011
- ^ Dr. Lara Sristava, European Commission Internet of Things Conference in Budapest, 16 May 2011 The Internet of Things – Back to the Future (Presentation)
- ^ P. Magrassi, A. Panarella, N. Deighton, G. Johnson, Computers to Acquire Control of the Physical World, Gartner research report T-14-0301, 28 September 2001
- ^ a b Casaleggio Associati The Evolution of Internet of Things February 2011 [need quotation to verify]
- ^ a b "Gartner Says 6.4 Billion Connected "Things" Will Be in Use in 2016, Up 30 Percent From 2015". Gartner. 10 November 2015. Retrieved 21 April 2016.
- ^ More Than 30 Billion Devices Will Wirelessly Connect to the Internet of Everything in 2020, ABI Research
- ^ Fickas, S.; Kortuem, G.; Segall, Z. (13–14 October 1997). "Software organization for dynamic and adaptable wearable systems". International Symposium on Wearable Computers: 56–63. doi:10.1109/ISWC.1997.629920. ISBN 0-8186-8192-6.
- ^ "Main Report: An In-depth Look at Expert Responses". Pew Research Center: Internet, Science & Tech. 14 May 2014. Retrieved 26 June 2015.
- ^ "Behind The Numbers: Growth in the Internet of Things". platform. Retrieved 26 June 2015.
- ^ "Budget 2015: some of the things we've announced". gov.uk. GOV.UK. Retrieved 31 March 2015.
- ^ Kushalnagar, N; Montenegro, G; Schumacher, C (August 2007). "IPv6 over Low-Power Wireless Personal Area Networks (6LoWPANs): Overview, Assumptions, Problem Statement, and Goals". Ietf Rfc 4919.
- ^ a b Sun, Charles C. (1 May 2014). "Stop using Internet Protocol Version 4!". Computerworld.
- ^ a b Sun, Charles C. (1 May 2014). "Stop Using Internet Protocol Version 4!". CIO. Retrieved 28 January 2015.
- ^ a b Sun, Charles C. (2 May 2014). "Stop using Internet Protocol Version 4!". InfoWorld.
- ^ a b Sun, Charles C. (1 May 2014). "Stop using Internet Protocol Version 4!". IDG News India.
- ^ a b c d e f g h i j k l Ersue, M; Romascanu, D; Schoenwaelder, J; Sehgal, A (4 July 2014). "Management of Networks with Constrained Devices: Use Cases". IETF Internet Draft < draft-ietf-opsawg-coman-use-cases>.
- ^ Vongsingthong, S.; Smanchat, S. (2014). "Internet of Things: A review of applications & technologies" (PDF). Suranaree Journal of Science and Technology.
- ^ Mitchell, Shane; Villa, Nicola; Stewart-Weeks, Martin; Lange, Anne. "The Internet of Everything for Cities: Connecting People, Process, Data, and Things To Improve the 'Livability' of Cities and Communities" (PDF). Cisco Systems. Retrieved 10 July 2014.
- ^ Narayanan, Ajit. "Impact of Internet of Things on the Retail Industry". PCQuest. Cyber Media Ltd. Retrieved 20 May 2014.
- ^ CasCard; Gemalto; Ericsson. "Smart Shopping: spark deals" (PDF). EU FP7 BUTLER Project.
- ^ Kyriazis, D.; Varvarigou, T.; Rossi, A.; White, D.; Cooper, J. (4–7 June 2013). "Sustainable smart city IoT applications: Heat and electricity management & Eco-conscious cruise control for public transportation". IEEE International Symposium and Workshops on a World of Wireless, Mobile and Multimedia Networks (WoWMoM): 1. doi:10.1109/WoWMoM.2013.6583500. ISBN 978-1-4673-5827-9.
- ^ Witkovski, Adriano (2015). "An IdM and Key-based Authentication Method for providing Single Sign-On in IoT!Proceedings of the IEEE GLOBECOM" (PDF): 1. doi:10.1109/GLOCOM.2015.7417597. ISBN 978-1-4799-5952-5.
{{cite journal}}: Cite journal requires|journal=(help) - ^ Clark, Liat. "Oxford Nanopore: we want to create the internet of living things". Wired UK. Wired UK. Retrieved 8 December 2015.
- ^ "Making your home 'smart', the Indian way". The Times of India. Retrieved 26 June 2015.
- ^ Perera, Charith; Liu, Harold; Jayawardena, Srimal (2015). "The Emerging Internet of Things Marketplace From an Industrial Perspective: A Survey". Emerging Topics in Computing, IEEE Transactions on. PrePrint (4): 585. doi:10.1109/TETC.2015.2390034. Retrieved 1 February 2015.
- ^ Couldry, Nick; Turow, Joseph (2014). "Advertising, Big Data, and the Clearance of the Public Realm: Marketers' New Approaches to the Content Subsidy". International Journal of Communication. 8: 1710–1726.
- ^ Moss, Jamie. "The internet of things: unlocking the marketing potential". theguardian.com. The Guardian. Retrieved 31 March 2015.
- ^ Meadows-Klue, Danny. "A new era of personal data unlocked in an "Internet of Things"". Digital Strategy Consulting. Retrieved 26 January 2015.
- ^ Millman, Rene. "6 real-life examples of IoT disrupting retail". Internet of Business. Retrieved 21 February 2016.
- ^ Davies, Nicola. "How the Internet of Things will enable 'smart buildings'". Extreme Tech.
- ^ Li, Shixing; Wang, Hong; Xu, Tao; Zhou, Guiping (2011). "Application Study on Internet of Things in Environment Protection Field". Lecture Notes in Electrical Engineering Volume. Lecture Notes in Electrical Engineering. 133: 99–106. doi:10.1007/978-3-642-25992-0_13. ISBN 978-3-642-25991-3.
- ^ FIT French Project. "Use case: Sensitive wildlife monitoring". Retrieved 10 July 2014.
- ^ K., Hart, Jane; Kirk, Martinez, (1 May 2015). "Toward an environmental Internet of Things". doi:10.1002/2014EA000044.
{{cite journal}}: Cite journal requires|journal=(help)CS1 maint: extra punctuation (link) CS1 maint: multiple names: authors list (link) - ^ a b Gubbi, Jayavardhana; Buyya, Rajkumar; Marusic, Slaven; Palaniswami, Marimuthu (24 February 2013). "Internet of Things (IoT): A vision, architectural elements, and future directions". Future Generation Computer Systems. 29 (7): 1645–1660. doi:10.1016/j.future.2013.01.010.
- ^ Chui, Michael; Löffler, Markus; Roberts, Roger. "The Internet of Things". McKinsey Quarterly. McKinsey & Company. Retrieved 10 July 2014.
- ^ Postscapes. "Smart Trash". Retrieved 10 July 2014.
- ^ Severi, S.; Abreu, G.; Sottile, F.; Pastrone, C.; Spirito, M.; Berens, F. (23–26 June 2014). "M2M Technologies: Enablers for a Pervasive Internet of Things". The European Conference on Networks and Communications (EUCNC2014).
- ^ Tan, Lu; Wang, Neng (20–22 August 2010). "Future Internet: The Internet of Things". 3rd International Conference on Advanced Computer Theory and Engineering (ICACTE). 5: 376–380. doi:10.1109/ICACTE.2010.5579543. ISBN 978-1-4244-6539-2.
- ^ "Center for Intelligent Maintenance Systems — IMS Center". www.imscenter.net. Retrieved 8 March 2016.
- ^ Lee, Jay (1 December 2003). "E-manufacturing—fundamental, tools, and transformation". Robotics and Computer-Integrated Manufacturing. Leadership of the Future in Manufacturing. 19 (6): 501–507. doi:10.1016/S0736-5845(03)00060-7.
- ^ a b c Daugherty, Paul; Negm, Walid; Banerjee, Prith; Alter, Allan. "Driving Unconventional Growth through the Industrial Internet of Things" (PDF). Accenture. Retrieved 17 March 2016.
- ^ a b Lee, Jay; Bagheri, Behrad; Kao, Hung-An (2015). "A cyber-physical systems architecture for industry 4.0-based manufacturing systems". Manufacturing Letters. 3: 18–23. doi:10.1016/j.mfglet.2014.12.001.
- ^ Lee, Jay (2015). Industrial Big Data. China: Mechanical Industry Press. ISBN 978-7-111-50624-9.
- ^ Accenture. "Industrial Internet Insights Report" (PDF). Retrieved 17 March 2016.
- ^ a b Lee, Jay (19 November 2014). "Keynote Presentation: Recent Advances and Transformation Direction of PHM". Roadmapping Workshop on Measurement Science for Prognostics and Health Management of Smart Manufacturing Systems Agenda. NIST.
- ^ a b Parello, J.; Claise, B.; Schoening, B.; Quittek, J. (28 April 2014). "Energy Management Framework". IETF Internet Draft <draft-ietf-eman-framework-19>.
- ^ Istepanian, R.; Hu, S.; Philip, N.; Sungoor, A. (30 August – 3 September 2011). "The potential of Internet of m-health Things "m-IoT" for non-invasive glucose level sensing". Annual International Conference of the IEEE Engineering in Medicine and Biology Society (EMBC): 5264. doi:10.1109/IEMBS.2011.6091302. ISBN 978-1-4577-1589-1.
- ^ Swan, Melanie (8 November 2012). "Sensor Mania! The Internet of Things, Wearable Computing, Objective Metrics, and the Quantified Self 2.0". Sensor and Actuator Networks. 1 (3): 217–253. doi:10.3390/jsan1030217.
{{cite journal}}: CS1 maint: unflagged free DOI (link) - ^ Rico, Juan (22–24 April 2014). "Going beyond monitoring and actuating in large scale smart cities". NFC & Proximity Solutions – WIMA Monaco.
- ^ "Sino-Singapore Guangzhou Knowledge City: A vision for a city today, a city of vision tomorrow". Retrieved 11 July 2014.
- ^ "San Jose Implements Intel Technology for a Smarter City". Retrieved 11 July 2014.
- ^ Coconuts Singapore. "Western Singapore becomes test-bed for smart city solutions". Retrieved 11 July 2014.
- ^ Lipsky, Jessica. "IoT Clash Over 900 MHz Options". EETimes. EETimes. Retrieved 15 May 2015.
- ^ Alleven, Monica. "Sigfox launches IoT network in 10 UK cities". Fierce Wireless Tech. Fierce Wireless Tech. Retrieved 13 May 2015.
- ^ Merritt, Rick. "13 Views of IoT World". EETimes. EETimes. Retrieved 15 May 2015.
- ^ Fitchard, Kevin. "Sigfox brings its internet of things network to San Francisco". Gigaom. Gigaom. Retrieved 15 May 2015.
- ^ "STE Security Innovation Awards Honorable Mention: The End of the Disconnect". Retrieved 12 August 2015.
- ^ Franceschi-Bicchierai, Lorenzo. "When the Internet of Things Starts to Feel Like the Internet of Shit". Motherboard. Vice Media Inc. Retrieved 27 June 2016.
- ^ Serebrin, Jacob. "Connected Lab Picks Up Where Xtreme Labs Left Off". Techvibes. Techvibes Inc. Retrieved 27 June 2016.
- ^ Porup, J.M. ""Internet of Things" security is hilariously broken and getting worse". Ars Technica. Condé Nast. Retrieved 27 June 2016.
- ^ Dan Brickley et al., c. 2001
- ^ Waldner, Jean-Baptiste (2008). Nanocomputers and Swarm Intelligence. London: ISTE. pp. 227–231. ISBN 1-84704-002-0.
- ^ "EPCIS – EPC Information Services Standard". GS1. Retrieved 2 January 2014.
- ^ Miles, Stephen B. (2011). RFID Technology and Applications. London: Cambridge University Press. pp. 6–8. ISBN 978-0-521-16961-5.
- ^ C.Alippi: Intelligence for Embedded Systems. Springer Verlag, 2014, 283pp, ISBN 978-3-319-05278-6.
- ^ Philippe Gautier, "RFID et acquisition de données évènementielles : retours d'expérience chez Bénédicta", pages 94 à 96, Systèmes d'Information et Management – revue trimestrielle N°2 Vol. 12, 2007, ISSN 1260-4984 / ISBN 978-2-7472-1290-8, éditions ESKA. [3]
- ^ Philippe GAUTIER (17 April 2010). "3 questions to Philippe GAUTIER, by David Fayon (from the original interview by David Fayon)" (in French: – I-O-T : INTERNET Of THINGS / Internet des Objets). Retrieved 26 June 2015.
{{cite web}}: External link in|type= - ^ Charith Perera; Arkady Zaslavsky; Peter Christen; Dimitrios Georgakopoulos (2013). "Context Aware Computing for The Internet of Things: A Survey". Communications Surveys Tutorials, IEEE. PP (n/a): 1–44. doi:10.1109/SURV.2013.042313.00197.
{{cite journal}}: Unknown parameter|last-author-amp=ignored (|name-list-style=suggested) (help) - ^ Pal, Arpan (May–June 2015). "Internet of Things: Making the Hype a Reality" (PDF). IT Pro. IEEE Computer Society. Retrieved 10 April 2016.
- ^ Gautier, Philippe; Gonzalez, Laurent (2011). L'Internet des Objets... Internet, mais en mieux (PDF). foreword by Gérald Santucci (European commission), postword by Daniel Kaplan (FING) and Michel Volle. Paris: AFNOR editions. ISBN 978-2-12-465316-4.
- ^ Waldner, Jean-Baptiste (2007). Nanoinformatique et intelligence ambiante. Inventer l'Ordinateur du XXIeme Siècle. London: Hermes Science. p. 254. ISBN 2-7462-1516-0.
- ^ "OGC SensorThings API standard specification | OGC". Retrieved 15 February 2016.
- ^ "OGC Sensor Web Enablement: Overview And High Level Architecture | OGC". Retrieved 15 February 2016.
- ^ "The Enterprise Internet of Things Market – Business Insider". Business Insider. 25 February 2015. Retrieved 26 June 2015.
- ^ Olga Kharif (8 January 2014). "Cisco CEO Pegs Internet of Things as $19 Trillion Market". Bloomberg.com. Retrieved 26 June 2015.
- ^ "Internet of Things: The "Basket of Remotes" Problem". Monday Note. Retrieved 26 June 2015.
- ^ "Better Business Decisions with Advanced Predictive Analytics". Intel. Retrieved 26 June 2015.
- ^ "Tech pages/IoT systems". Retrieved 26 June 2015.
- ^ Want, Roy; Bill N. Schilit, Scott Jenson (2015). "Enabling the Internet of Things". Vol. 1. Sponsored by IEEE Computer Society. IEEE. pp. 28–35.
- ^ Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. (1 January 2015). "Internet of Things: A Survey on Enabling Technologies, Protocols, and Applications". IEEE Communications Surveys Tutorials. 17 (4): 2347–2376. doi:10.1109/COMST.2015.2444095. ISSN 1553-877X.
- ^ "The Internet of Things: a jumbled mess or a jumbled mess?". The Register. Retrieved 5 June 2016.
- ^ "Can we talk? Internet of Things vendors face a communications 'mess'". Computerworld. Retrieved 5 June 2016.
- ^ "Top Five Things to Know about Cisco BiDi Optical Technology White Paper - Cisco". 5 September 2014. Retrieved 6 May 2016.
40-Gbps bidirectional (BiDi) optical technology
- ^ Clausen, T.; Colin de Verdiere, A.; Yi, J.; Niktash, A.; Igarashi, Y.; Satoh, H.; Herberg, U.; Lavenu, C.; Lys, T.; Dean, J. (2016). The Lightweight On-demand Ad hoc Distance-vector Routing Protocol - Next Generation (LOADng). IETF. I-D draft-clausen-lln-loadng-14. Retrieved 10 May 2016.
{{citation}}: Unknown parameter|month=ignored (help) - ^ Winter, T.; Thubert, P.; Brandt, A.; Hui, J.; Kelsey, R.; Levis, P.; Pister, K.; Struik, R.; Vasseur, JP.; Alexander, R. (2012). RPL: IPv6 Routing Protocol for Low-Power and Lossy Networks. IETF. doi:10.17487/RFC6550. RFC 6550. Retrieved 10 May 2016.
{{citation}}: Unknown parameter|month=ignored (help) - ^ Philip N. Howard, The Internet of Things is Posed to Change Democracy Itself, Politico, 2015.06.01
- ^ [4]
- ^ http://fortune.com/2016/04/06/who-owns-the-data/
- ^ http://www.mhc.ie/latest/blog/the-internet-of-things-legal-challenges-in-an-ultra-connected-world?utm_source=Mondaq&utm_medium=syndication&utm_campaign=View-Original
- ^ https://www.itu.int/en/ITU-D/Conferences/GSR/Documents/GSR2015/Discussion_papers_and_Presentations/GSR_DiscussionPaper_IoT.pdf
- ^ https://www.ftc.gov/news-events/press-releases/2015/01/ftc-report-internet-things-urges-companies-adopt-best-practices
- ^ http://www.mis-asia.com/tech/internet/iot-users-could-win-with-a-new-bill-in-the-us-senate/
- ^ http://www.lexology.com/library/detail.aspx?g=fd6bc26e-dd20-4c4f-897a-5d62484d37ba
- ^ http://www.mobileworldlive.com/mwc16-articles/iot-experts-fret-over-fragmentation/ IoT experts fret over fragmentation
- ^ https://www.qualcomm.com/news/onq/2016/02/19/fragmentation-enemy-internet-things Fragmentation is the enemy of the Internet of Things
- ^ http://www.mckinsey.com/industries/semiconductors/our-insights/internet-of-things-opportunities-and-challenges-for-semiconductor-companies Internet of Things: Opportunities and challenges for semiconductor companies
- ^ https://evothings.com/will-fragmentation-of-standards-only-hinder-the-true-potential-of-the-iot-industry/ Will fragmentation of standards only hinder the true potential of the IoT industry?
- ^ http://www.arm.com/zh/files/event/ATF2015SZ_A6_Thundersoft.pdf IOT Brings Fragmentation in Platform
- ^ https://www.w3.org/Talks/2016/04-27-countering-fragmentation.pdf Countering Fragmentation with the Web of Things
- ^ Steve Kovach (30 July 2013). "Android Fragmentation Report". Business Insider. Retrieved 19 October 2013.
- ^ https://www.linux.com/news/who-needs-internet-things Who Needs the Internet of Things?
- ^ https://www.linux.com/NEWS/21-OPEN-SOURCE-PROJECTS-IOT 21 Open Source Projects for IoT
- ^ http://techbeacon.com/will-android-fragmentation-spoil-its-iot-appeal Will Android fragmentation spoil its IoT appeal?
- ^ Franceschi-Bicchierai, Lorenzo. "Goodbye, Android". Motherboard. Vice. Retrieved 2 August 2015.
- ^ Kingsley-Hughes, Adrian. "The toxic hellstew survival guide". ZDnet. Retrieved 2 August 2015.
- ^ Tung, Liam (13 October 2015). "Android security a 'market for lemons' that leaves 87 percent vulnerable". zdnet.com. ZDNet. Retrieved 14 October 2015.
- ^ Thomas, Daniel R.; Beresford, Alastair R.; Rice, Andrew. "Security Metrics for the Android Ecosystem" (PDF). Computer Laboratory, University of Cambridge. doi:10.1145/2808117.2808118. Retrieved 14 October 2015.
- ^ Philip N. Howard, Pax Technica: How the Internet of Things May Set Us Free, Or Lock Us Up. New Haven, CT: Yale University Press, 2015.
- ^ Adrian McEwan (2014). "Designing the Internet of Things" (PDF). Retrieved 1 June 2016.
- ^ "Connected Things and Civic Responsibilities". Retrieved 20 May 2016.
- ^ "Panopticon as a metaphor for the Internet of Things" (PDF). The Council of the Internet of Things. Retrieved 6 June 2016.
- ^ a b "Notice" (PDF).
- ^ "Notice" (PDF).
- ^ Yoshigoe, Kenji; Dai, Wei; Abramson, Melissa; Jacobs, Alexander (2015). "Overcoming Invasion of Privacy in Smart Home Environment with Synthetic Packet Injection". TRON Symposium (TRONSHOW): 1. doi:10.1109/TRONSHOW.2014.7396875. ISBN 978-4-8936-2317-1.
- ^ Verbeek, Peter-Paul. "Moralizing Technology: Understanding and Designing the Morality of Things." Chicago: The University of Chicago Press, 2011.
- ^ Diane Cardwell, At Newark Airport, the Lights Are On, and They're Watching You, The New York Times, 2014.02.17
- ^ Hardy, Quentin (4 February 2015). "Tim O'Reilly Explains the Internet of Things". The New York Times Bits. The New York Times. Retrieved 18 May 2015.
- ^ Webb, Geoff (5 February 2015). "Say Goodbye to Privacy". WIRED. Retrieved 15 February 2015.
- ^ Catherine Crump and Matthew Harwood, The Net Closes Around Us, TomDispatch, 25 March 2014
- ^ Perera, Charith; Ranjan, Rajiv; Wang, Lizhe; Khan, Samee; Zomaya, Albert (2015). "Privacy of Big Data in the Internet of Things Era". IEEE IT Professional Magazine. arXiv:1412.8339.
- ^ Brown, Ian (12 February 2013). "Britain's Smart Meter Programme: A Case Study in Privacy by Design" – via papers.ssrn.com.
- ^ a b https://www.bcs.org/upload/pdf/societal-impact-report-feb13.pdf
- ^ Singh, Jatinder; Pasquier, Thomas; Bacon, Jean; Ko, Hajoon; Eyers, David (2015). "Twenty Cloud Security Considerations for Supporting the Internet of Things". IEEE Internet of Things Journal. 3 (3): 1–1. doi:10.1109/JIOT.2015.2460333.
- ^ Chris Clearfield. "Why The FTC Can't Regulate The Internet Of Things". Forbes. Retrieved 26 June 2015.
- ^ "We Asked Executives About The Internet Of Things And Their Answers Reveal That Security Remains A Huge Concern". Business Insider. Retrieved 26 June 2015.
- ^ Christopher Clearfield "Rethinking Security for the Internet of Things" Harvard Business Review Blog, 26 June 2013/
- ^ A. Witkovski; A. O. Santin; J. E. Marynowski; V. Abreu Jr. (December 2016), An IdM and Key-based Authentication Method for providing Single Sign-On in IoT (PDF), IEEE Globecom
- ^ Joseph Steinberg (27 January 2014). "These Devices May Be Spying On You (Even In Your Own Home)". Forbes. Retrieved 27 May 2014.
- ^ Andy Greenberg (21 July 2015). "Hackers Remotely Kill a Jeep on the Highway—With Me in It". Wired. Retrieved 21 July 2015.
- ^ Scientific American, April 2015, page 68
- ^ Loukas, George (June 2015). Cyber-Physical Attacks A growing invisible threat. Oxford, UK: Butterworh-Heinemann (Elsevier). p. 65. ISBN 9780128012901.
- ^ SCIENTIFIC AMERICAN, November 2015, page 30
- ^ Disruptive Technologies Global Trends 2025. National Intelligence Council (NIC), April 2008, P. 27.
- ^ Ackerman, Spencer (15 March 2012). "CIA Chief: We'll Spy on You Through Your Dishwasher". WIRED. Retrieved 26 June 2015.
- ^ "Smart devices to get security tune-up". BBC News.
- ^ "IoT Security Foundation – Executive Steering Board". IoT Security Foundation.
- ^ Roy Thomas Fielding, Architectural Styles and the Design of Network-based Software Architectures (2000), Dissertation – Doctor of Philosophy in Information and Computer Science
- ^ Littman, Michael and Samuel Kortchmar. "The Path To A Programmable World". Footnote. Retrieved 14 June 2014.
- ^ Finley, Klint (6 May 2014). "The Internet of Things Could Drown Our Environment in Gadgets". Wired.
- ^ "The time that Tony Fadell sold me a container of hummus". 3 April 2016. Retrieved 7 April 2016.
- ^ a b c Kit Walsh (5 April 2016). "Nest Reminds Customers That Ownership Isn't What It Used to Be". Retrieved 7 April 2016.
- ^ "Peter Day's World of Business". BBC World Service. BBC. Retrieved 4 October 2016.
Further reading
This article needs attention from an expert on the subject. The specific problem is: This list needs to be de-spammed and trimmed down to the three most essential books on this topic only. (September 2016) |
- Chaouchi, Hakima. The Internet of Things. London: Wiley-ISTE, 2010.
- Chabanne, Herve, Pascal Urien, and Jean-Ferdinand Susini. RFID and the Internet of Things. London: ISTE, 2011.
- Hersent, Olivier, David Boswarthick and Omar Elloumi. The Internet of Things: Key Applications and Protocols. Chichester, West Sussex: Wiley, 2012.
- Pfister, Cuno. Getting Started with the Internet of Things. Sebastapool, Calif: O'Reilly Media, Inc., 2011.
- Uckelmann, Dieter, Mark Harrison and Florian Michahelles. Architecting the Internet of Things. Berlin: Springer, 2011.
- Weber, Rolf H., and Romana Weber. Internet of Things: Legal Perspectives. Berlin: Springer, 2010.
- Zhou, Honbo. The Internet of Things in the Cloud: A Middleware Perspective. Boca Raton: CRC Press, Taylor & Francis Group, 2013.
External links
This article's use of external links may not follow Wikipedia's policies or guidelines. (September 2016) |
- "A New Economic Vision for Addressing Climate Change (Internet of things – part II)". Huffington Post. 2 June 2014. (2014-06-02) and "Monopoly Capitalism vs. Collaborative Commons (Internet of things – part I)". Huffington Post. 7 April 2014. (2014-04-07)
- Pew Internet canvas of experts, prognosticating on the nature, application, and impact of the Internet of Things in 2025
- "The Creepy New Wave of the Internet (Internet of things)". (2014-11-02), New York Review of Books
- The IoT Council
- Internet of Things and People research center at Malmö University, Sweden
- Internet of Things could get big with battery free Devices powered by Wi-Fi signals. (PoWi-Fi).
- IoT and Last Mile Navigation
- Ramsey, Rachel. "PubNub Brings Reliable, Real-time Connectivity to the IoT with Connected Car Solution Kit". (2014-01-29), IoT Evolution World
