SYN flood

A SYN flood is a form of denial-of-service attack in which an attacker sends a succession of SYN requests to a target's system in an attempt to consume enough server resources to make the system unresponsive to legitimate traffic.
Technical details
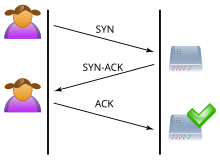
Normally when a client attempts to start a TCP connection to a server, the client and server exchange a series of messages which normally runs like this:
- The client requests a connection by sending a
SYN(synchronize) message to the server. - The server acknowledges this request by sending
SYN-ACKback to the client. - The client responds with an
ACK, and the connection is established.
This is called the TCP three-way handshake, and is the foundation for every connection established using the TCP protocol.
A SYN flood attack works by not responding to the server with the expected ACK code. The malicious client can either simply not send the expected ACK, or by spoofing the source IP address in the SYN, causing the server to send the SYN-ACK to a falsified IP address - which will not send an ACK because it "knows" that it never sent a SYN.
The server will wait for the acknowledgement for some time, as simple network congestion could also be the cause of the missing ACK, but in an attack increasingly large numbers of half-open connections will bind resources on the server until no new connections can be made, resulting in a denial of service to legitimate traffic. Some systems may also malfunction badly or even crash if other operating system functions are starved of resources in this way.
Countermeasures
There are a number of well-known countermeasures listed in RFC 4987 including:
- Filtering
- Increasing Backlog
- Reducing SYN-RECEIVED Timer
- Recycling the Oldest Half-Open TCP
- SYN Cache
- SYN cookies
- Hybrid Approaches
- Firewalls and Proxies
See also
- Denial-of-service attack
- IP address spoofing
- Internet Control Message Protocol
- Ping flood
- UDP flood attack
- Fraggle attack
- Smurf attack
References
